SAP Cloud Identity Access Governance provides real-time access governance and continuous monitoring of user access by immediately calculating the access analysis results as a background activity. Organizations can choose one or all of the services of SAP Cloud Identity Access Governance, depending on their business needs. It can easily be extended across the enterprise as the business grows.
Key Concept
SAP Cloud Identity Access Governance is an SAP HANA Cloud Platform solution. Its main tasks are to optimize user access and identity management and to provide governance and ensure compliance with legal regulations and industry and company policies. SAP Cloud Identity Access Governance assists users in analyzing critical access risks, mitigating access risks, and performing segregation of duties (SoD) analysis.
Currently, two services are available in SAP Cloud Identity Access Governance:
- Cloud Single Sign-On (manage the identity life cycle in the cloud)
- SAP Cloud Identity Access Governance, access analysis service
Two other services are expected to be released in 2017:
- User Provisioning service
- Role Designer service
Figure 1 shows the features of SAP Cloud Identity Access Governance, access analysis service.

Figure 1
SAP Cloud Identity Access Governance, access analysis service features
Table 1 shows a high-level summary and comparison of SAP Access Control and SAP Cloud Identity Access Governance, access analysis service.
| Topic, feature capability |
SAP Access Control |
SAP Cloud Identity Access Governance, access analysis service
|
|
Strategic positioning
|
A well-established and widely used foundation in the SAP GRC and security portfolio. A strategic solution for addressing access control requirements.
|
A brand-new solution offering a low-cost entry point to managing identity and access governance requirements in the cloud. Fast to deploy, quick time to value. One service of a larger planned SAP Cloud Identity Access Governance solution set.
|
Functional capabilities
|
Comprehensive access control capabilities, especially when used with solution extensions by Greenlight. Functional capability:
•Access Analysis
•Access Management/User Provisioning
•Business Role Design
•Access Certification
• Emergency Access Management
|
Functionality designed specifically to deliver Access Analysis capabilities, including:
• Critical access use analysis
• Critical access risk analysis
• Access risk remediation
• Segregation of duties (SoD) analysis
• SoD risk assessment
|
Target market
segments
|
SAP and non-SAP large enterprises
• Typically, more comfortable with on-premise or hosted environments
• Organizations that need comprehensive identity and access governance
• Possibly with existing investments in on-premise solutions from SAP
|
SAP and non-SAP subject matter experts (SMEs) and some large enterprises
• Organizations that have made the strategic decision to move to the cloud
• Organizations reviewing competitive cloud access governance solutions
• Organizations that have already invested in SAP Cloud Identity Access Governance
|
Table 1
A comparison of SAP Access Control and SAP Cloud Identity Access Governance, access analysis service
SAP Cloud Identity Access Governance, Access Analysis Service Features
Here are details about the main features that are available as part of the SAP Cloud Identity Access Governance, access analysis service:
- Audit and reporting. Analytic-based dashboard reports are available for administrators to get a high-level overview of the data.
- Analyze access. Event-driven access analysis and risk scores (calculated based on user access, use, risks, and mitigation) help to identify the changes that are relevant for access risk rules and process them in near real time. There is no delay in responding to the access violations, and therefore, access risks can be mitigated more quickly and easily, with less chance of an adverse impact on the business.
- Refine users and roles. An option is available to refine the user’s risk at run time by adding or removing certain roles.
- Simplified mitigation. The mitigation process is more simplified by giving the control selection option by user and risk.
Architecture Overview
Figure 2 shows the high-level architecture of SAP Cloud Identity Access Governance. With the multitenant architecture, it is designed to provide every tenant a dedicated share of the instance, including its data, configuration, user management, and tenant individual functionality. SAP HANA Cloud Platform smart process services enable you to build applications that process streams of incoming data in real time and to collect and act on incoming information. Apache Olingo provides the collection of Java libraries for implementing OData. SAP HANA Cloud Platform is certified to support the Java EE 6 Web Profile. It supports the micro-services architecture wherein the services can be deployed independently.

Figure 2
SAP Cloud Identity Access Governance architecture
The SAP Cloud Identity Access Governance, access analysis service is the main focus of SAP Cloud Identity Access Governance. It consists of three major steps:
- Synchronize the data between back-end operational systems and the repository
- Execute the permission assessment for changed roles
- Perform access analysis
Figure 3 is the home page of SAP Cloud Identity Access Governance that can be accessed via a URL. There are four headers available in the home page: Access Analysis, Reports, Administration, and Help.
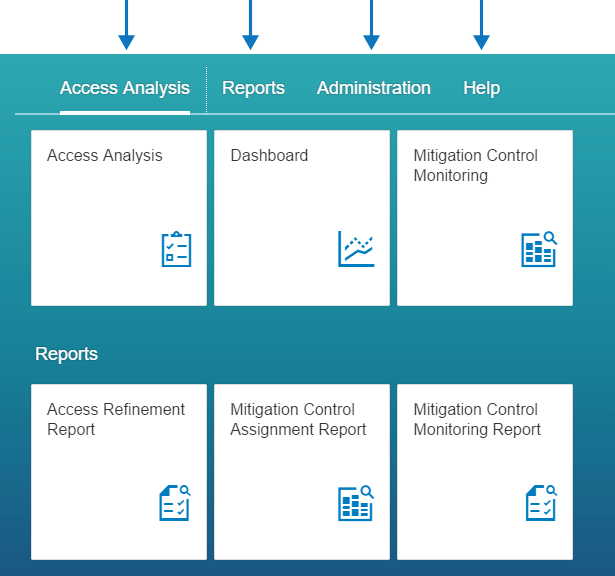
Figure 3
The SAP Cloud Identity Access Governance home page
The Access Analysis Tile
When you click the Access Analysis tile, it shows the details of the user’s SoD risk and critical access risk (Figure 4).
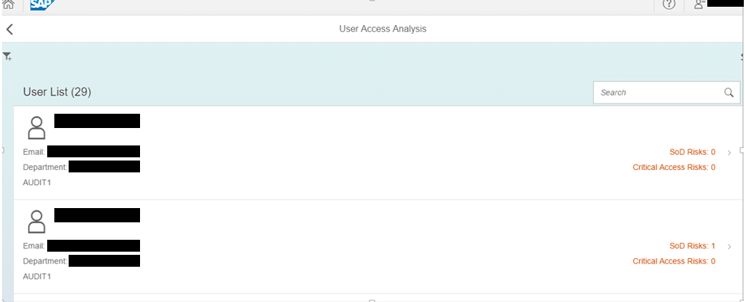
Figure 4
User Access Analysis details
After you click the user name, you can view the details of the access assigned to the user. As shown in Figure 5, this page has the details of a user’s access and risks.

Figure 5
User access and risk detail
Remediation of the risks can be done from the same page by clicking the Remediate button. Clicking this button associates a remediation tag with the mitigation control as shown in Figure 6. The mitigation details can be viewed any time using this tag.

Figure 6
Remediation tag
The option to refine the risk also is available, as shown in Figure 5. After clicking the Refine link, you can enter refinement proposals to reduce the number of risks as shown in Figure 7. With the Refinement proposal a user or administrator can see how many risks can be added or removed by adding or removing certain roles to or from the user. (In Figure 7 a user who has a greater number of risks is selected.)
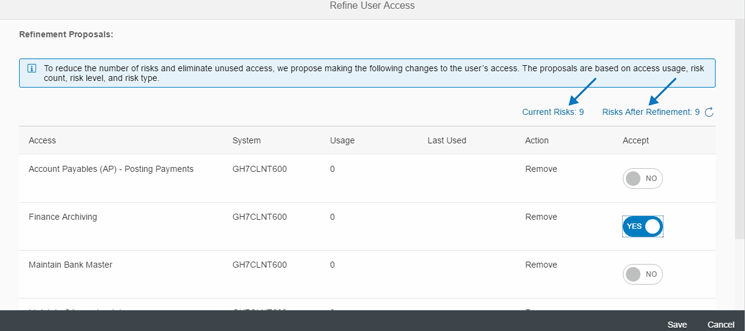
Figure 7
Access refinement
You set the Accept flag as Yes or No for the Action Remove and save it by clicking the Save button shown in Figure 7. After you click the Save button to save the refinement data, you can compare the difference in the risks by checking the current risks and risks after the refinement link as shown in Figure 7. With refinement you can check how many risks will be reduced or increased if a particular role is removed or added. The current risk shows the number of risks initially available for the user and Risk after refinement shows the number of risks available after adding or removing certain roles from a user account by setting the accept flag as Yes or No for the action Remove.
After the data is saved in Figure 7, the user is redirected to Figure 5, which shows the user access and risk detail. In the screen shown in Figure 5 you can assign mitigation control and monitor groups to risks by navigating to the Risk area (by clicking the RISKS hyperlink) as shown in Figure 8.
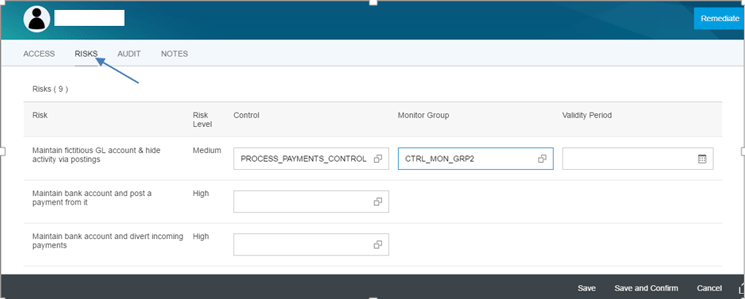
Figure 8
Risk mitigation
You can view the complete audit information related to all the actions performed under the AUDIT section as shown in Figure 9.

Figure 9
Audit information
Figure 10 shows the overall process of the SAP Cloud Identity Access Governance, access analysis service.

Figure 10
SAP Cloud Identity Access Governance, access analysis service process overview
Dashboard
In the Access Analysis Overview dashboard (you access it by clicking the Dashboard tile in the home page screen), you can view five different types of information together as shown in Figure 11:
- By Risk Score
- Risk Trend by Quarter
- Business Processes with the most Risks
- Risk Occurrences
- Risks by Risk Level
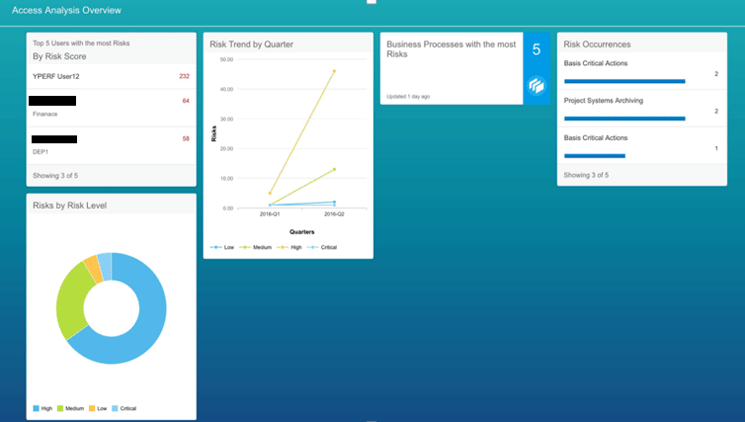
Figure 11
The Access Analysis Overview dashboard
Mitigation Control Monitoring
Under Mitigation Control Monitoring (you access it by clicking the Mitigation Control Monitoring tile in the home page screen), you can create test plans for periodic assessment of the mitigation controls.
Reports
SAP Cloud Identity Access Governance reports are available under the second header (Reports) in the home page as shown in Figure 12.
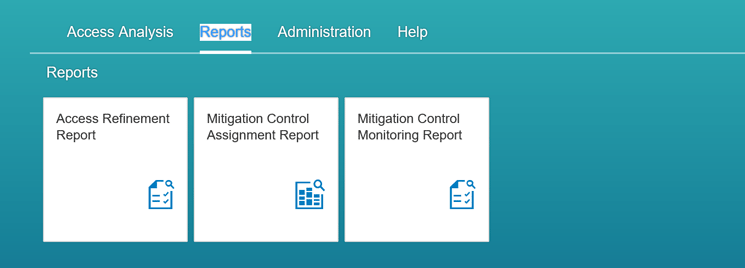
Figure 12
SAP Cloud Identity Access Governance reports
SAP Cloud Identity Access Governance provides the following reports:
- Access Refinement Report: This report shows all the data corresponding to the remediation tags defined under User Access Analysis.
- Mitigation Control Assignment Report: This report shows the details of the Mitigation Control Assignment, their validity dates, and the associated remediation tags.
- Mitigation Control Monitoring Report: This report shows the mitigation control test results on the basis of a mitigation control ID. With each mitigation control, there is an associated control ID.
Administration
Figure 13
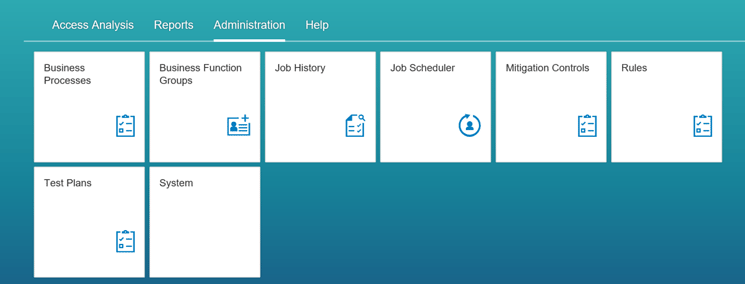
Figure 13
SAP Cloud Identity Access Governance Administration
This data needs to be set up prior to the use of SAP Cloud Identity Access Governance as master data, similar to what used to be done in SAP Access Control.
The objects that you can create under the Administration header include:
- Business process: Business process data entries can be created and maintained to help analyze the desired access risk.
- Business function groups: Business function groups are logical groups that have back-end systems assigned to them. Under the Administration header you can create a business function group and assign systems to it.
- Job history: Different job logs and details can be viewed under job history. It is only for the purpose of viewing.
- Job scheduler: Available jobs (pre-delivered jobs that are shipped with the product) can be scheduled under job scheduler.
- Mitigation controls: Mitigation controls can be created and maintained (master data) for access risks that cannot be eliminated.
- Rules: Rules can be maintained for SoD and critical access risks. These rules can be assigned to target system groups.
- Test plans: Test plans can be created for periodic assessment of mitigation controls.
- System: Target systems can be configured and maintained.
Neha Garg
Neha Garg, senior developer, SAP Labs India Pvt. Ltd., has nine years of experience in SAP Labs. Neha is currently working with the Installed Base Maintenance Support (IMS) organization, SAP Labs, India, for SAP Access Control 5.3, 10.0, and 10.1. Neha has vast experience and has worked on multiple technologies, including JavaScript, Java, web services, OData services, SAPUI5, HANA, ABAP WebDynpro, Floor Plan Manager with ABAP WD, ABAP OO, SAP ABAP dictionary, and function modules for a broad range of SAP modules and SAP Access Control. Neha has worked in almost all the sub-components of SAP Access Control and has published one patent in the SAP Access Control area.
You may contact the author at neha.garg@sap.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the editor.






















