Nitin Aggarwal and Sanjeev Kotwal show how to use the training verification functionality in SAP Access Control to automate the training check in the user access provisioning process.
Key Concept
SAP Access Control is used to provision roles or profiles to users in back-end systems in a compliant way. Every request for access submitted in SAP Access Control goes through a pre-defined approval process composed of approvers such as manager, role owner, compliance team, or system owner. One of these approvals could be training managers in companies that require users to undertake a training course before access is granted.
More and more companies have started using SAP Access Control to automate compliance checks, but very rarely have we come across companies using the full potential of the tool. One such functionality is training verification. It offers a vast scope of automation in the user access provisioning process, but is often not used by companies. The use of training verification functionality can automate the training check in the user access provisioning process, thereby reducing the manual work of checking the training completion as well as improving compliance. We present the different options available to automate the training check using your SAP Access Control system.
Common Configuration
The configuration steps that we describe in this section need to be done whether or not you choose to set up training verification in SAP Access Control.
SAP Access Control Configuration Settings
There are two ways to connect to a training verification system from SAP Access Control—a Business Add-In (BAdI) or web services.
Follow menu path SPRO > Governance, Risk and Compliance > Access Control > Maintain Configuration Settings to define the method of checking the training records from the training system. In the screen that follows, choose the value for Parameter ID 2024 (Access Request Training Verification) as shown in Figure 1. Based on our experience, we recommend that you choose the BAdI option unless the training system is a web-based system. In a web-based system only a web service call can be made from the SAP Access Control system. We recommend a BAdI as it is easy to implement and troubleshoot in the case of SAP ABAP-based systems. (SAP Access Control 10 and 10.1 are based on SAP ABAP. The older version 5.3 was Java based.)

Figure 1
Parameter setup
Connector Setup
The next step is to create a connector for the training system where training records are stored. The SAP Access Control system can use this connection to automatically check the availability of training records for users in the workflow process. Use transaction code SM59 to create a connector.
In the case of a BAdI, as shown in Figure 2, use Connection Type 3. In the case of a web service, as shown in Figure 3, use Connection Type G.

Figure 2
Create a connector for training verification using a BAdI

Figure 3
Create a connector for training verification using a web service
Prerequisite Configuration
SAP Access Control offers a variety of prerequisites, such as training, certification, and non-disclosure agreements, that can be used in roles for different purposes. In our scenario we use the training prerequisite as we want to automate the training check.
Step 1. Define a new prerequisite type for the training check. To complete this step, follow menu path SPRO > Governance, Risk and Compliance > Access Control > Role Management > Define Prerequisite types. In the screen that appears (Figure 4), enter the short description (Prereq Typ) and long description (Prerequisite Type) of the training prerequisite.
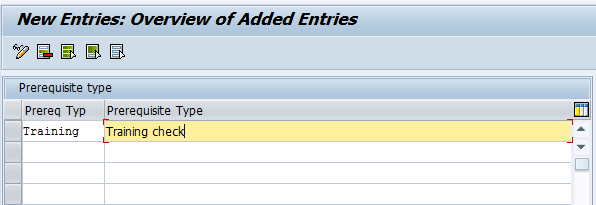
Figure 4
Define the prerequisite types
Step 2. Define a new prerequisite for roles that need mandatory training before assignment to a user. To complete this step, follow menu path SPRO > Governance, Risk and Compliance > Access Control > Role Management > Define Role Prerequisites. In Figure 5, enter the required details. (The Prerequisite Type defined in Figure 4 and the training system defined in Figures 2 or 3 need to be selected.)

Figure 5
Define role prerequisites
Repeat this step for each prerequisite or training course that needs to be checked in SAP Access Control.
BAdI Implementation
Execute transaction code SE18 to implement BAdI GRAC_TRG_VERIF. Enter the name of the BAdI as shown in Figure 6. This BAdI enables the training verification by connecting to the training system.
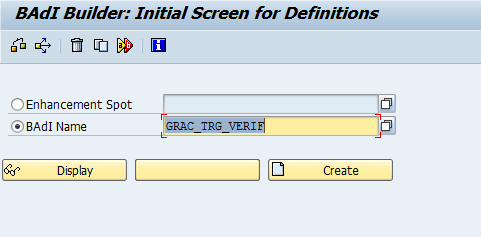
Figure 6
Enter the BAdI name
Click the Create button. This takes you to Figure 7. Enter the names of the Enhancement Implementation and Short Text and click the enter icon (the green checkmark). This action takes you to the screen shown in Figure 8.
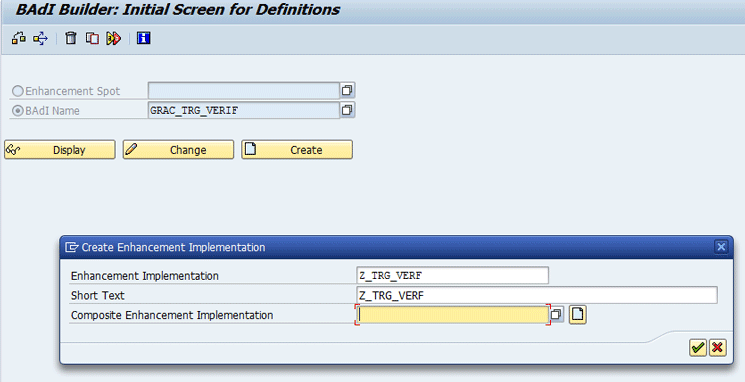
Figure 7
Create a custom enhancement implementation

Figure 8
Create a local implementation of the BAdI
In the Implementing Class field, enter the name of the custom class as shown in Figure 8. Double-click the name of the Implementing Class and implement your custom logic in the VERIFY method by clicking the Method name. The VERIFY method is present in the interface IF_GRAC_TRG_VERIF that we implemented in the custom class Z_TRG_VERIF. Double-clicking the VERIFY method takes you to the ABAP editor where you can write your custom ABAP code. In this example, we called a Remote Function Call (RFC) created in the training system, which returns a success message if the training has been done.
The custom logic carries details of the function module that will be called from SAP Access Control to the training system for verification. Details such as User name, Role name, Training course ID, and Training system name need to be sent to the training system using this method. In return, the training system returns training success or failure status messages. After the approval of roles by the role managers is done in the SAP Access Control system, request data is passed to the training system to check the training status of the roles requested in the access request. Training statuses are sent back to the SAP Access Control system as the return information.
Web Service Implementation
To use a web service for training verification, you first need to create a logical port for the Proxy class CO_GRAC_AR_ROLVERIFY_WEBSERVIC using transaction code LPCONFIG. A logical port is a port required to retrieve run-time settings to connect to web services. In Figure 9 choose the Proxy Class, and in the Logical Port field, enter the same name as the name of the connector created earlier in Figure 3. Click the create icon.
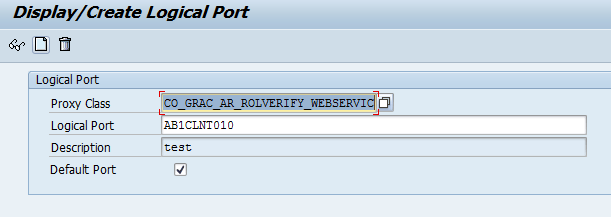
Figure 9
Create a logical port
In the initial screen that appears, go to the General Settings section and click the Call Parameters tab (Figure 10). Enter data in HTTP Destination and Path Suffix fields as shown in the screenrprint. The HTTP Destination has to be the connector, and the Path Suffix is the custom web service created in the training system to verify training requirements. The training system is the system for which we created a connection in Figure 3. The web service is created in the training system or is available by standard in the training system depending on the type of training system.

Figure 10
Maintain call parameters in the logical port
Details such as User name, Role name, Training course ID, Request number, and company need to be sent to the training system using this web service. In return, the training system returns training success or failure through the web service itself.
Different Options to Enable a Training Verification Check
SAP Access Control provides two options to enable the training verification check—check at request submission or check after an approval stage in multi-stage multi-path (MSMP) workflow. Following are the details for enabling these checks.
Option 1: Training Verification at Request Submission
When you use the option to check at request submission, the system performs a check for training at the time of submission of the request. The system uses a BAdI or web service to call the training system. A check is performed for training completion for all the roles that have a training prerequisite active in the role master data. In case the training system returns a failure for one or more roles selected in the request, the system displays an error message and does not allow the requestor to submit the request.
Go to the SAP Access Control system and choose Access Management > Role Maintenance (Figure 11). To use this verification option, set the training prerequisite to active in the role master data by selecting the Active check box. Set the Verify on Request drop-down option to Yes as shown in Figure 11.
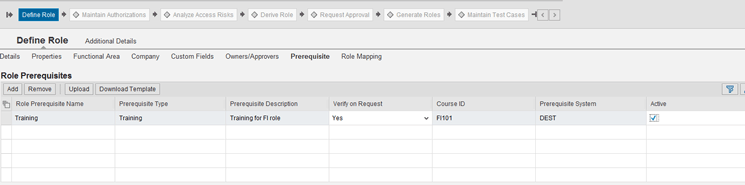
Figure 11
Prerequisite in role master data with Verify on request active
Option 2: Training Verification After an Approval Stage in MSMP
When you use the second option, the system performs a check for training after a predefined approval stage in MSMP workflow. The system uses a BAdI or a web service to call the training system, and a check is performed for training completion for all the roles that have a training prerequisite active in the role master data.
In case the training system returns a failure for one or more roles selected in the request, the system routes the request or role to a detour path. To use this option, go to the SAP Access Control system and choose the Access Management > Role Maintenance option. Set the training prerequisite to active in the role master data by selecting the Active check box and set the Verify on Request option to No as shown in Figure 12.
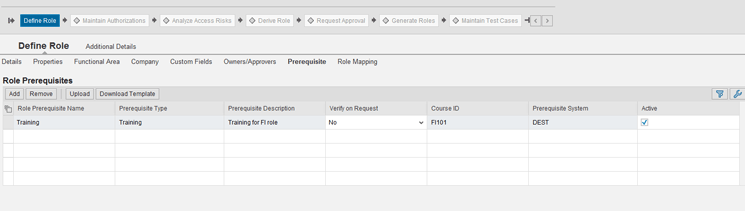
Figure 12
Prerequisite in role master data with Verify on Request inactive
You also need to set up the Rule ID GRAC_MSMP_DETOUR_TRG_VERIF in the MSMP workflow. You do so by linking it to a stage in the workflow at the Maintain Paths step of MSMP workflow configuration, as shown in Figure 13. To do this you need to open the MSMP workflow configuration page by following the menu path SPRO > Governance, Risk and Compliance > Access Control > Workflow for access control > Maintain MSMP workflows. This routing rule enables the request to be sent to a detour path in case the training system returns a failure for training check.
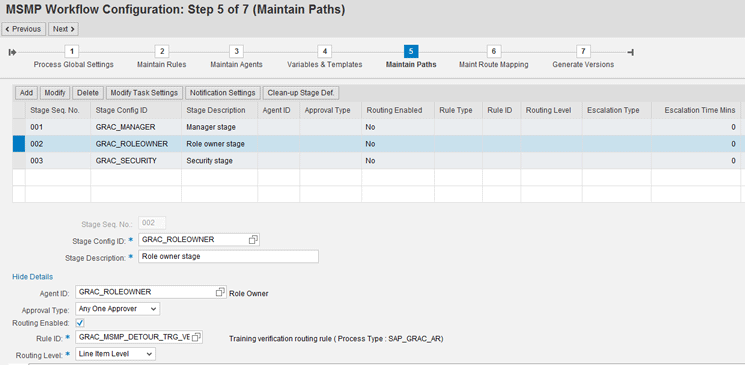
Figure 13
Set up the routing rule for training verification
We set up the detour rule in the role owner stage, which is in the second row in Figure 13. The system checks for training after the role owner approval stage.
Note
The configuration of MSMP workflows in SAP Access Control is beyond the scope of this article.
The Routing Level option in this setup controls whether the complete request is routed to the detour path or if only the roles for which training has failed are routed to the detour path. The Routing Level set at the Stage Level routes the complete request to the detour path, whereas the Routing Level set as Line Item Level only moves the individual roles to the detour path.
The detour path needs to be specified in the Maintain Route Mapping step of the MSMP workflow configuration as shown in Figure 14. To do this you need to open the MSMP workflow configuration page by following menu path SPRO > Governance, Risk and Compliance > Access Control > Workflow for access control > Maintain MSMP workflows.

Figure 14
Maintain route mapping
Nitin Aggarwal
Nitin Aggarwal is a chartered accountant and a certified information systems auditor with more than 10 years of experience in SAP implementations, business process control reviews, access and authorizations reviews, and IT audit. He is a subject matter expert on SAP Access Control and has been involved in numerous implementations over the past seven years.
You may contact the author at Nitin_Aggarwal09@infosys.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the editor.
Sanjeev Kotwal
Sanjeev Kotwal is an ABAP technical consultant with more than five years of experience in SAP implementations. His areas of expertise include Web Dynpro ABAP, SAP Adobe forms, BSP, user exits, and report programming.
You may contact the author at sanjeev_kotwal@infosys.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the editor.
























