Learn how to achieve efficient, compliant, and secure management of user accounts and identities with SAP NetWeaver Identity Management (SAP NetWeaver IDM). Step through an overview of SAP NetWeaver IDM, including the product’s architecture and integration capabilities.
Key Concept
SAP NetWeaver Identity Management (SAP NetWeaver IDM) provides provisioning capabilities for SAP and third-party applications. You can integrate it with SAP BusinessObjects Access Control to comply with regulatory requirements and build a solid foundation for an identity infrastructure.
SAP NetWeaver Identity Management (SAP NetWeaver IDM) 7.1 has worked out many of the initial hiccups of its predecessor, SAP NetWeaver IDM 7.0, and is designed to establish compliant and business-driven identity management by:
- Centralizing management of user identities for SAP and non-SAP systems
- Providing compliant end-to-end automation for user identities via integration with SAP BusinessObjects GRC solutions and SAP ERP
- Enabling role-based access controls
- Leveraging rule-driven workflow/approval processes
SAP NetWeaver IDM also seeks to produce efficiencies, strengthen accountability, and extend the IT systems support of businesses within the areas depicted in Figure 1. SAP NetWeaver IDM provides enhanced control for user identities within an SAP ERP landscape, including end-to-end compliant user provisioning, while minimizing time and cost.

Figure 1
SAP NetWeaver IDM impact
We’ll review the technical components of SAP NetWeaver IDM before explaining how it integrates with SAP BusinessObjects Access Control. Then we’ll walk you through three production and non-production scenarios to show you how it works in business terms.
Technical Components
The core components of SAP NetWeaver IDM are the Identity Center (IC) and the Virtual Directory Server (VDS). The IC is the primary component used for identity management. It includes functions for identity provisioning, workflow, password management, logging, and reporting. It uses a centralized repository called the identity store to provide a uniformed view of the data, regardless of the data’s original source.
For the IC to carry out these IDM functions, it must retrieve data from various repositories, consolidate it, and transform it into the necessary formats so the data is accepted when it is published back to the various decentralized repositories. The way the IC accomplishes this is by relying on the activities of the VDS.
The VDS acts as a single access point for clients retrieving or updating data in multiple data repositories, as it provides a uniformed view of the data in real time (i.e., continual synchronization with connected systems). For example, you can use the VDS to consolidate multiple repositories and then serve as a data source for the IC. The IC can then proceed with the user provisioning and identity management functions using the consolidated data produced by the VDS. This relationship is outlined in the architectural diagram shown in Figure 2.
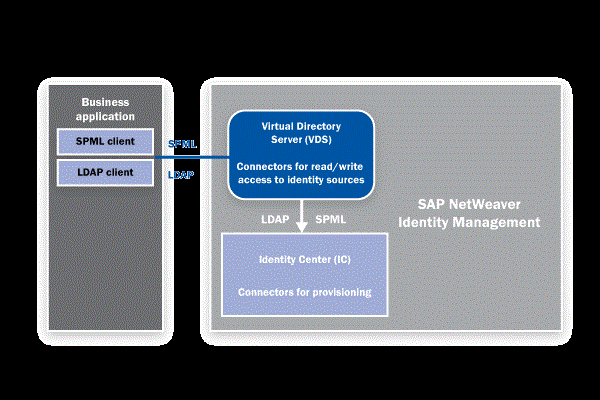
Figure 2
SAP NetWeaver IDM architecture
The VDS includes the following key capabilities:
- Combines disparate data sources in a virtual directory tree
- Flexible access control
- Extensive authentication mechanisms
- Extensive server configuration possibilities
- Schema adaptations
- Attribute value modifications
- Namespace conversion
- Access to data sources using Java classes
-
Caches search results
Integration Architecture
While the IC and VDS components can work standalone, SAP has also developed open standards-based integration points for both SAP and non-SAP applications. This is accomplished using SAP NetWeaver Process Integration (SAP NetWeaver PI), which provides identity as a service. This enables the extension of the user repository to the SAP Enterprise Services Repository tool, which allows SAP NetWeaver IDM to communicate with multiple supported connectors in an IT organization.
This technique allows companies to achieve an enterprise service-oriented architecture with total integration. You can see a high-level overview of the SAP NetWeaver PI integration architecture in Figure 3. You can also see a complete list of the connectors that this architecture supports in Figure 4.

Figure 3
SAP NetWeaver IDM and SAP NetWeaver PI integration architecture

Figure 4
SAP NetWeaver IDM supported connectors
In addition to SAP NetWeaver PI and the Enterprise Services Repository, SAP NetWeaver IDM is also staged to easily integrate with SAP BusinessObjects GRC solutions. Leveraging the access control characteristics of the GRC suite, the installation of SAP NetWeaver IDM is designed for end-to-end compliant identity management that results in:
- Increased security administration efficiencies for a reduced total cost of ownership
- Integration with SAP BusinessObjects Access Control for compliance with segregation of duties (SoD) and sensitive access requirements
- Integrated view of current and historic access rights, approvals, and policy violations
Many of the features enabled by SAP BusinessObjects GRC solutions integration are outlined in the “Additional Solution Highlights” section of this article. Figure 4 shows how SAP NetWeaver IDM is used in tandem with SAP BusinessObjects Access Control.
Figure 5 shows the list of SAP and third-party directory servers, databases, platforms, and applications with which SAP NetWeaver IDM integrates.
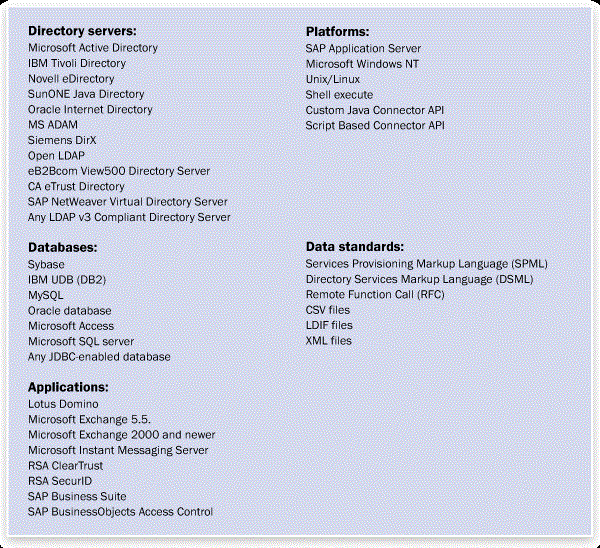
Figure 5
Systems with which SAP BusinessObjects IDM integrates
Additional Solution Highlights
SAP NetWeaver IDM is designed to allow companies to move away from purely technical account management and implement a compliant identity management solution to manage the entire life cycle of employees, partners, and customers. This includes the following components:
- Password management: Many help desk calls concern forgotten passwords. The IC includes a kiosk solution for resetting lost passwords. A user who forgets his or her password can log on with a given user name and reach the workflow’s password recovery task without gaining access to any other resources. This provides a secure way for recovering passwords without assistance from a help desk or another internal service desk.
- Reporting and auditing: SAP NetWeaver IDM is designed to provide reporting options that, when accessed, can provide a means for supporting an organization’s audit practices. SAP NetWeaver IDM includes a standard set of canned reports and also provides the ability to build custom reports using the different log repositories. You can execute reports on demand or schedule them to run in a batch. Example report content includes user and system access profiles, data modification tracking, approval history, SoD, and user tasks performed.
- Provisioning, workflow, and approvals: Customizable workflow features have been built into the IC. You can send messages and execute actions with these workflows. The workflow logic supports users that are requesting and approving access as well as situations that require users to be informed or alerted. Using the security role access logic and SAP NetWeaver IDM connectors, user provisioning is also automated during the completion of a workflow.
-
Provision access by role: The IC component helps you build both business roles and technical roles. You can establish business roles in a hierarchy fashion to define the separation of business tasks among users. These business roles are then mapped to technical roles within the IC to provide the necessary security authorizations within the child ABAP, SAP NetWeaver Portal, User Management Engine (UME), and other Java-based systems. You can either upload or refresh technical roles from the child systems directly or rebuild them in the IC to mirror the technical roles that exist in the child systems.
Sample SAP NetWeaver IDM Scenarios
You can use SAP NetWeaver IDM as an accelerator and an identity enablement tool throughout the full project life cycle of an SAP implementation. Once configured, it can help streamline IDM activities across all connected systems. The following scenarios provide examples of this — the first three are non-production scenarios, and the last three are production scenarios.
Non-Production Scenario 1: A New Consultant Joins the XYZ Team on a Major Implementation Project
Using SAP NetWeaver IDM, the technical support team initiates a request for the creation of an active directory account to establish the new consultant’s identity for use in the project systems. Once approved via a custom workflow path, SAP NetWeaver IDM provisions all downstream access (e.g., ID creation, role assignment, security parameters) based on the security profile defined in the IC business role that was selected for the XYZ team member.
Sample Technical Solution for Non-Production Scenario 1
Using SAP Net Weaver IDM, the technical support team initiates an access request task (i.e., ordered task) that may include an approval task for required approvals and a provisioning task (i.e., action task) for provisioning required access after approval. You can initiate the access request from the end user menu, which you need to configure within the Access Control tab. By configuring policies, you can make the request functionality available to all or a limited set of users.
A predefined business role for Active Directory is configured in the IC and selected as part of the request. As part of the configuration, an approval task is associated with the main request for approval. A defined set of approvers can be configured within SAP NetWeaver IDM. A provisioning task is attached to the main task for provisioning access. This task uses a preconfigured scheduled job to provision access. All of the above processes are tied to a notification task that notifies all stakeholders about the status of the request.
Non-Production Scenario 2: A Project Consultant Moves from the FI Team to the Integration Team
The project’s integration team manager submits an access change request through Compliant User Provisioning (CUP), a component of SAP BusinessObjects Access Control. Once approved, the SAP NetWeaver IDM-to-CUP integration triggers a task configured for employee access transfer within the development and quality assurance SAP environments that support the project integration test cycles. SAP NetWeaver IDM expires the employee’s Finance Support roles and provides the corresponding data integration team with an SAP composite role as defined within a job-to-role mapping table.
Sample Technical Solution for Non-Production Scenario 2
Via the integration of CUP and SAP NetWeaver IDM, tasks are executed based on different triggers within CUP. The role change request submitted by the manager in CUP triggers an approval process enabled via CUP’s internal workflow engine.
Once approval has been granted, the request is forwarded to SAP NetWeaver IDM and triggers a pre-configured role change task. (Pre-configured, out-of-the-box tasks are available in SAP NetWeaver IDM, but they can also be customized to fit companies’ unique requirements.) The task evaluates the access to be granted or removed (using an additional conditional task) based on access-role mapping defined in SAP NetWeaver IDM.
The task removes the Finance Support roles and related access by triggering a de-provisioning task (available out of the box) for the Finance Support roles. Similarly, SAP NetWeaver IDM also triggers a provisioning task for the integration team roles based on the access-role mapping. If a notification is required, a notification task is also created and associated with the existing role change task.
Non-Production Scenario 3: A Consultant Leaves the Project
The project management office is informed of a consultant’s project departure date and coordinates a request through the manual paper-based access form process that is still being used while the company is implementing the latest version of CUP. On the paper form, the consultant’s client counterpart neglects to indicate that in addition to non-production SAP ERP Central Component (SAP ECC) access, the consultant was also provisioned a UME portal administrator account. When the SAP NetWeaver IDM separation workflow is initiated, both the UME administrator account and the non-production SAP ECC system access are revoked accordingly.
Sample Technical Solution for Non-Production Scenario 3
The project management office can use the SAP NetWeaver IDM end user interface to initiate a request for separation of a consultant. Triggers from VDS are detected by SAP NetWeaver IDM, which initiates a separation task in the background. A conditional task determines what user access is to be removed based on the termination date defined for the user.
SAP NetWeaver IDM identifies all security roles assigned to the consultant by retrieving a list of all assigned roles in SAP NetWeaver IDM. A de-provisioning task is triggered for each assigned security role and access is automatically removed. A notification task is used to notify the user’s manager about the access removal.
Production Scenario 1: New Employee X Requires Financial Analyst Role Access to Perform the Month-End Close
Employee X is hired and an HR analyst creates an employee record within SAP ERP Human Capital Management (SAP ERP HCM). An automatic job triggers an import to SAP NetWeaver IDM. SAP NetWeaver IDM receives the updates from SAP ERP HCM and creates an entry for Employee X in SAP NetWeaver IDM. This results in the creation of Active Directory, ABAP, and UME accounts with the role Financial Analyst. SAP NetWeaver IDM then sends an email notification to Employee X’s manager that includes Employee X’s detailed credentials.
When the month-end close approaches, Employee X’s manager submits a request for the Month-End Close security role in both SAP ECC and SAP NetWeaver IDM. Employee X’s manager also decides to request a Procurement role for Employee X in anticipation of a future responsibility the employee may require. The request for both roles is forwarded to CUP for SoD analysis. SAP BusinessObjects Access Control completes the risk analysis and notifies the risk owner about any SoD violations resulting from the user’s current access and the additional request for the Month-End Close and Procurement security roles. The risk owner is notified via CUP’s automated email workflow and reviews and approves the request. SAP NetWeaver IDM retrieves the request status information and the status of the SoD analysis from SAP BusinessObjects Access Control. Since SoD analysis has been performed and the results have been approved, SAP NetWeaver IDM provisions the two new roles in the SAP systems.
Sample Technical Solution for Production Scenario 1
SAP NetWeaver IDM is configured to trigger a custom task when there is a request for additional access. SAP NetWeaver IDM forwards the request to CUP via Web service calls (preconfigured in the SAP BusinessObjects Access Control framework). CUP completes the SoD analysis for the newly-created security roles via its integration with Risk Analysis and Remediation (RAR) and returns the results.
The risk owner has the ability to accept or mitigate the risk and approve the security role addition within the CUP workflow engine. SAP NetWeaver IDM checks the status of the request for approval or rejection via Web service calls. Once it is approved by the risk owner, SAP NetWeaver IDM provisions the Month-End Close and Procurement security roles to Employee X.
Production Scenario 2: A New Security Role in SAP ECC Needs to Be Assigned to an Enterprise Role in SAP NetWeaver IDM
A new security role AP_Manager_Display is created in SAP ECC. SAP NetWeaver IDM pulls the new role details from SAP ECC as part of a scheduled interface process. The security administrator associates the new role with the position AP Clerk in SAP NetWeaver IDM. SAP NetWeaver IDM pushes the data to CUP for risk analysis and notifies the risk owner about any SoD violations. The risk owner reviews and approves the request. CUP assigns the new security role to the corresponding position in SAP ERP HCM.
Sample Technical Solution for Production Scenario 2
SAP NetWeaver IDM is configured to trigger a custom task called AP Clerk when there is an addition of any new security roles to an enterprise role. When the AP_Manager_Display security role is added to the AP Clerk enterprise role, SAP NetWeaver IDM runs a task to check possible SoD violations in SAP BusinessObjects Access Control via Web service calls (pre-configured in the SAP BusinessObjects Access Control framework). If any SoD conflict exists, SAP BusinessObjects Access Control notifies the risk owner to mitigate the risk.
The risk owner can accept or mitigate the risk and approve the security role addition within CUP.
SAP NetWeaver IDM checks the status of the request for approval or rejection via Web service calls. Once it is approved by the risk owner, SAP NetWeaver IDM updates the AP Clerk enterprise role to include the AP_Manager_Display security role. SAP NetWeaver IDM runs a script to identify users assigned the AP Clerk Enterprise Role and triggers a task to provision each user with the AP_Manager_Display role.
Production Scenario 3: Employee X Returns from an Extended Leave to a Temporary Suspension of Access
Corporate policy 810 of Corporation Y mandates that all employees change their passwords every 60 days. Employee X returns from an extended leave of absence and receives notification that his Active Directory password has expired, thus implementing a temporary suspension of the employee’s access in all downstream systems.
Employee X accesses the SAP NetWeaver IDM portal that is linked to Corporation Y’s intranet. Employee X browses the profile page on the portal with the intention of updating his password profile. Once submitted, the password task on SAP NetWeaver IDM triggers an update to the user’s password in the other connected systems, including the Active Directory, UNIX, a SQL database, SAP ECC, and SAP NetWeaver Business Warehouse (SAP NetWeaver BW).
Sample Technical Solution for Production Scenario 3
SAP NetWeaver IDM is configured to provide a link for changing or resetting passwords on multiple systems. When Employee X accesses SAP NetWeaver IDM’s user interface and clicks to change his password, a change password task is triggered. The change password task identifies all systems where the employee’s password needs to be changed and also checks the new password against a central password policy. If the password provided by Employee X does not match the policy, the change password task prompts the employee to provide a valid password. (Password fields can be configured to check against policy.)
If the password matches the existing policy, the change password task triggers separate jobs to change the password on all systems. You can configure a change password job for each type of system (e.g., Active Directory, UNIX, database, and SAP systems). Once the password is changed on all systems, the employee is notified of the password change via a notification task.
Chris Knapik
Chris Knapik is a senior consultant with Deloitte & Touche LLP’s security & privacy group with four years of consulting experience. Originally a native of Ohio, Chris began his career with Deloitte & Touche LLP in Chicago with a focus on SAP Sarbanes-Oxley attestation work. It was here Chris obtained his CISA certification and joined Deloitte’s security and privacy services practice. Chris now resides in Orlando, Florida, and is staffed on large-scale SAP implementation projects in the consumer and industrial products industry.
You may contact the author at cknapik@deloitte.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the editor.
Mira Doneva
Mira Doneva is a manager with Deloitte & Touche LLP’s security and privacy group. She has more than six years of experience in SAP security and GRC implementations, information system audits, and business process reviews. Her SAP security experience includes role design, configuration, and user administration for various SAP modules, including SAP BusinessObjects Access Control and SAP NetWeaver Identity Management. Her audit experience includes multiple Sarbanes-Oxley IT audits and business cycle reviews for various IT environments, including SAP. Mira has worked on projects in the manufacturing, healthcare, retail, financial services, telecommunications, and energy industries. She is a certified information system security professional (CISSP) and a certified information systems auditor (CISA).
You may contact the author at mdoneva@deloitte.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the editor.
Debi Mohanty
Debi Mohanty is a manager with Deloitte & Touche LLP’s security and privacy group based out of Deloitte’s India office. He has more than nine years of experience in identity and access management. His experience includes strategy and implementation of solutions around identity life cycle management, access control, role design, and user access certification for various applications, including SAP NetWeaver Identity Management. Debi has worked on projects in the utilities, healthcare, retail, financial services, and oil and gas industries.
You may contact the author at demohanty@deloitte.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the editor.









