Learn about options for combining SAP Access Control and SAP NetWeaver Identity Management to support automation of identity and access processes and compliance requirements within your organization.
Key Concept
An integrated software solution that combines SAP NetWeaver Identity Management and SAP Access Control enables you to automate access governance and identity management capabilities to support automation of identity and access processes and compliance requirements. SAP Access Control is based on ABAP technology and integrates with the native SAP ERP, Oracle, PeopleSoft, and JDE interfaces to support access governance capabilities. These capabilities include features such as administration of the access request process and approval process with integrated segregation of duties (SoD) analysis. SAP NetWeaver Identity Management is based on Java technology and is designed to support administration of user identities, user provisioning, and single sign-on (SSO) across IT systems and applications.
SAP Access Control provides highly specialized functionality required to administer access and manage accounts to meet requirements for financial regulations and company policies. SAP NetWeaver Identity Management (SAP NetWeaver ID Management) provides features designed to automate identity administration across multiple systems. When SAP NetWeaver ID Management is integrated with SAP Access Control, segregation of duties (SoD) analysis capabilities can be integrated with the approval processes within an identity management system to ensure that role assignments are compliant with financial regulations. Figure 1 outlines the features of SAP Access Control and SAP NetWeaver ID Management.
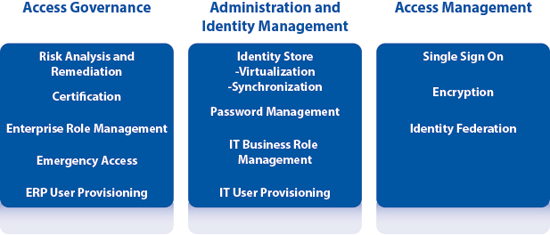
Figure 1
Features of SAP NetWeaver ID Management and SAP Access Control
SAP Netweaver ID Management
SAP NetWeaver ID Management provides a comprehensive solution for managing user accounts and privileges across enterprise landscapes. Enterprise landscapes include a variety of applications and systems such as Microsoft Active Directory, Microsoft Exchange, SAP Business Suite, and custom applications. SAP NetWeaver ID Management can integrate with these systems to support identity management and provisioning through a combination of out-of-the-box connectors, standards-based integration, connectors provided by partners, and connectors custom developed using SAP NetWeaver ID Management’s published connector application programming interface (API).
SAP NetWeaver ID Management supports the functionality to manage the user life cycle from initial onboarding, change, and termination. SAP NetWeaver ID Management includes an integrated workflow engine, extended role-based access control, and an integrated identity store built on virtual directory technology, the authoritative source for user identity data. SAP NetWeaver ID Management provides password synchronization functionality, allowing users to change their passwords on a number of source systems and have those passwords synchronized across all their different accounts. Comprehensive reporting of activities relating to the mappings of users, roles, and privileges are provided through SAP NetWeaver Business Warehouse.
Standards-based Web single sign-on (SSO) functionality is provided through a Security Assertion Markup Language (SAML) 2.0 compliant identity provider. In addition, the product includes a virtual directory software component that provides valuable meta-directory functionality and forms the engine for the product’s connector API.
SAP Access Control
SAP Access Control is an access governance solution that automates the processes associated with managing access to business applications. SAP Access Control supports processes and audit records that track who has access, who approved access, when the access was granted, and if the access assignments are still required.
SAP Access Control is designed to bridge the gap between obtaining the technical definitions of system authorizations and facilitating the process of associating the correct system authorization or entitlement with the appropriate user. SAP Access Control includes the following five modules to accomplish this automation:
- Access request process — integrated workflow process to orchestrate approvals, SoD analysis, account actions (i.e., create, delete, lock, unlock), and automated role assignment
- User, role, and risk certification — supports a periodic review process for existing user assignments, role definitions, and access risks required by several compliance regulations
- Risk analysis and remediation — enables analysis of SoD violations by role or business process. The integrated risk analysis enables stakeholders to resolve conflicts and reduce risk by mitigating the violation by changing the role assignment or through a mitigating control.
- Business role management — supports management of SAP technical and business role life cycle management. SAP Business Role Management enables the centralized management of SAP technical roles across multiple systems using a role methodology. This process ensures that roles are subjected to appropriate testing and approvals prior to deployment. Business roles in SAP BRM are groups of entitlements that can be associated with job functions for easily assignment to business users.
- Emergency access management — a complete solution for managing access for privileged user access with integrated monitoring and log review.
SAP Access Control is built on SAP ABAP technology and is supported using standard SAP Basis and transport processes. SAP Access Control is intentionally built as a stand-alone solution to support integrated compliance and access provisioning for SAP ERP systems.
Major Features
Table 1 compares key features of SAP NetWeaver ID Management and SAP Access Control.

Table 1
Feature comparison
Deployment Considerations
Because both SAP Access Control and SAP NetWeaver ID Management were designed as independent solutions, there are several options to consider when integrating SAP Access Control to an existing SAP NetWeaver ID Management deployment and vice versa. Along with these options are important considerations for approval processes and management of the integrated solution. Figure 2 shows the architecture of the integrated solution.
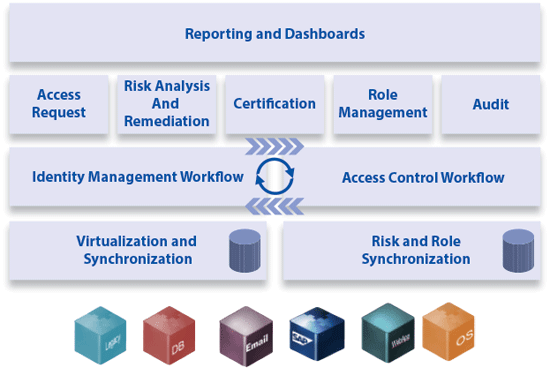
Figure 2
Architecture of the integrated SAP Access Control and SAP Netweaver ID Management solution
For organizations already using SAP Access Control, integration of SAP NetWeaver ID Management can enable common integrated workflow approval and provisioning process that includes IT, email, and business applications. You can initiate access requests in SAP NetWeaver ID Management with subsequent approvals and analysis in SAP Access Control. This solution helps to consolidate identity and access administration processes with automated workflow, provisioning, and integrated SoD analysis. Table 2 lists the considerations for implementing an integrated approval workflow for existing SAP Access Control users.

Table 2
Options for existing SAP Access Control customers
Companies already using SAP NetWeaver ID Management can benefit from integrating SAP Access Control to support access governance and compliance features required to manage access to the ERP system. SAP Access Control also includes role management, emergency access management, and reporting and audit features that enhance and expand the value of SAP NetWeaver ID Management.
Table 3 lists the considerations for integrating SAP Access Control with existing SAP NetWeaver ID Management deployments.
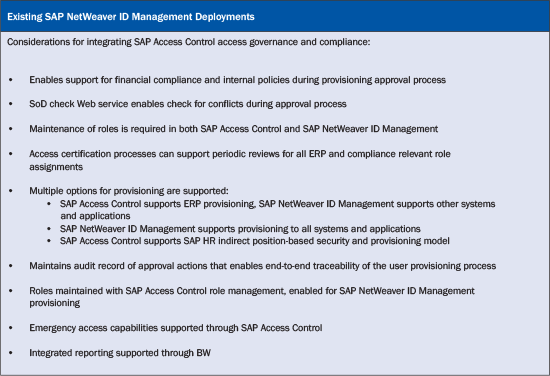
Table 3
Options for existing SAP NetWeaver ID Management customers
Case Study: Accenture
Accenture conducts business in more than 120 countries, and its annual revenue is approximately US$26 billion. It had six working days to close its accounting books. The company’s objectives were to achieve access risk as a part of the user provisioning process, reduce access risk and adverse compliance events across the enterprise, and perform real-time access risk analysis, alerts, and reporting by integrating with SAP NetWeaver ID Management.
Integration Scenario
In the scenario shown in Figure 3, SAP NetWeaver ID Management initiates a compliance check request to SAP Access Control. SAP Access Control remediates any access risk associated to the users’ request before handing it back to the identity management system to provision to SAP applications.

Figure 3
A Compliance Check Request
This scenario yields the following benefits:
- Lower cost of operations by automating manual processes
- A real-time view of system compliance and the ability to present this to auditors on demand
- An improved ability to respond to governance issues and potential violations
In many organizations, the management of IT systems and financial applications are supported by different organizations. However the processes are similar in some cases. The integrated solution of SAP NetWeaver ID Management and SAP Access Control enables organizations to share a common set of tools to manage IT and ERP access and identity built on common workflow, roles, and processes.
Swetta Singh
Swetta Singh is director of solution management, governance, risk and compliance at SAP Labs with over 13 years’ experience in IT industry focused on corporate governance, enterprise risk management and corporate compliance helping solve customer problems.
You may contact the author at Swetta.Singh@sap.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the editor.
Chris Radkowski
Chris Radkowski is director of solution management, governance, risk and compliance at SAP Labs with extensive experience in identity, access control, and security technologies. Chris is a frequent speaker at SAP events and driving several strategies for access control, compliance, and analytics.
You may contact the author at Chris.Radkowski@sap.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the editor.
Keith Grayson
Keith Grayson is a business development manager, EMEA at SAP with over 20 years’ experience in the IT industry. He is passionate about creating, articulating and realizing real business value with technology. Keith has a deep background in all aspects of IT security and particularly with identity and access management. He speaks about SAP’s Identity Management and GRC approach and strategy at analyst and industry events, particularly relating to articulating IT risk effectively in the context of overall corporate risk.
You may contact the author at Keith.Grayson@sap.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the editor.











