Sort out the authentication options offered for BusinessObjects Enterprise and see how to use them.
Key Concept
Authentication is the process of verifying the identity of a user who attempts to access the system.
This article was originally published on BusinessObjects Expert
SAP BusinessObjects Enterprise provides several authentication methods for enabling users to log on to the application and for providing secure report access. BusinessObjects contains its own user names and passwords as part of a security model known as enterprise authentication. The system also integrates with third-party authentication tools, including Microsoft Windows Active Directory (AD), Light-Weight Directory Access Protocol (LDAP), and SAP ERP systems.
Use of the external authentication tools eliminates the need to re-create and maintain individual user and group accounts within BusinessObjects Enterprise. This convenient feature saves time for both the administrator and end users of BusinessObjects Enterprise.
BusinessObjects Enterprise also supports single sign-on or trusted authentication for both the Windows NT and Windows AD methods, so users of BusinessObjects do not have to re-enter their log-on credentials after already logging on to the operating system. When a user logs on to the operating system, a security context for that user is created, and the user can seamlessly connect to BusinessObjects.
The reason BusinessObjects Enterprise supports several security models in addition to its own security model is simple: It is more efficient to use entities, such as user accounts and passwords that already exist outside of BusinessObjects Enterprise. Fortunately, none of these security options are mutually exclusive; they can all be used simultaneously.
Use of external entities does not mean that if Windows AD authentication is used administration is done exclusively from Windows AD. It simply implies that objects, such as user accounts and passwords, can be maintained within Windows AD, but BusinessObjects Enterprise feeds off those existing accounts when users try to log on. Security administrators still create and configure BusinessObjects Enterprise groups and objects, as well as relevant restrictions to those objects, from the BusinessObjects Central Management Console (CMC). Table 1 is an overview of the four types of authentication for accessing BusinessObjects Enterprise.
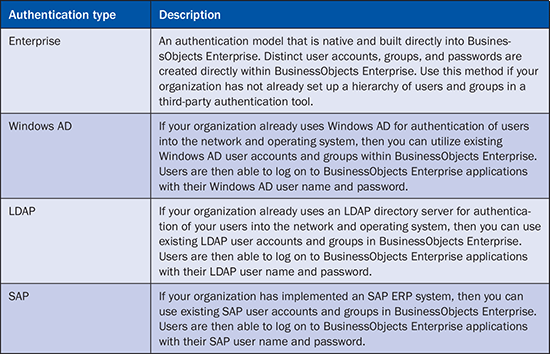
Table 1
Descriptions of authentication methods
Figure 1 shows the log-on screen for BusinessObjects Enterprise (i.e., the InfoView portal), which enables the user to enter a user name, password, and authentication method (Enterprise, LDAP, Windows AD, or SAP).

Figure 1
Log on to BusinessObjects Enterprise with an authentication method
Now I discuss each of these four authentication methods.
Enterprise Authentication
BusinessObjects Enterprise provides its own native security model, called enterprise authentication. Therefore, BusinessObjects Enterprise contains it own set of user, groups, and passwords and can operate without being integrated with a third-party security database that may also contain security information. Subsequently, the enterprise authentication model is the default security model used by BusinessObjects Enterprise. It does not require additional configuration after the completion of the initial installation of the product.
However, administrators can set configuration settings with enterprise authentication, including user password restrictions, user restrictions, and log-on restrictions. Selecting the Enterprise tab on the authentication page of the CMC enables an administrator to enforce rules relevant to enterprise authentication. Administrators can use this tab to control the frequency that users are forced to change their passwords, as well as the length of the passwords, whether the password must contain mixed-case letters, or when to disable or re-enable a user account (Figure 2).

Figure 2
Administrator settings for enterprise authentication in the CMC
LDAP Authentication
LDAP is a software protocol for enabling users with a network to locate organizations, individuals, and other resources — such as files and devices within that network — whether on the public Internet or on a corporate intranet. LDAP enables a network administrator to maintain a central directory server for managing user access to a variety of applications and operating systems. LDAP is a standard technology for network directories or specialized databases that store information about devices, applications, people, and other aspects of a computer network.
BusinessObjects Enterprise can integrate with an LDAP server for storage of user and password information. Thus, authentication of users is external to the BusinessObjects Enterprise application. However, with integration to LDAP, specific folder and object permissions (i.e., authorization) are still defined within BusinessObjects Enterprise. When BusinessObjects Enterprise is integrated with an LDAP server, equivalent BusinessObjects Enterprise accounts are either created if they don’t exist or aliased if they do exist.
The reason for this process is that the BusinessObjects Enterprise system must contain references to users and groups inside its own system so that report object restrictions are configured. However, with integration to LDAP, user passwords are not stored in BusinessObjects Enterprise, and it is the function of LDAP server to verify passwords. Any time a user attempts to access and log on to BusinessObjects Enterprise, a password confirmation request is sent to the LDAP server, and BusinessObjects Enterprise waits for successful confirmation of the request. If the user information authenticates properly in LDAP, then BusinessObjects Enterprise allows a connection and log-on.
Administrators can configure LDAP authentication by selecting the LDAP tab on the authentication page of the CMC. Table 2 shows the settings that are needed for the configuration of LDAP authentication within BusinessObjects Enterprise.
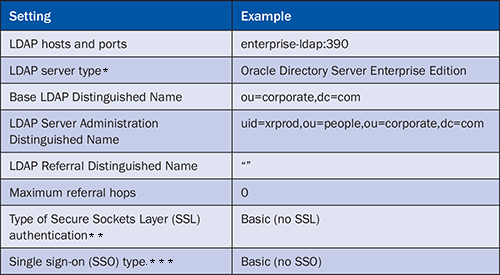
Table 2
Settings to configure LDAP authentication (see the note box below for details on the superscript references in the table)
Note
Table 1 includes the following superscript references:
* BusinessObjects Enterprise can integrate with the following LDAP server types:
- Oracle Directory Server Enterprise Edition (formerly Sun Directory Server)
- Lotus Domino Enterprise Server
- IBM Tivoli Directory Server
- Novell eDirectory
- Oracle Internet Directory
- Microsoft Windows AD Application
** Options for types of SSL authentication include:
- Basic (no SSL)
- Server authentication
- Mutual authentication
*** SSO types include:
- Basic (no SSO)
- SiteMinder
Windows AD Authentication
Windows AD is a directory and authentication service that Microsoft created for Windows domain networks. It is included within Windows Server operating systems. In addition, Windows AD provides a central location for network administration of users and passwords and functionality to authenticate and authorize all end users into a Windows-controlled network.
BusinessObjects Enterprise provides the capability to integrate end-user authentication with users and groups already set in an implementation of the Windows AD network management tool. Administrators can configure Windows authentication from the Windows AD tab of the authentication page of the CMC.
Administrators can configure Windows AD authentication by selecting the Windows AD tab on the authentication page of the CMC. Table 3 shows the settings that are needed for the configuration of Windows AD authentication within BusinessObjects Enterprise. To enable Windows authentication, select the Enable Windows Active Directory option at the top of the screen. Enter the name of Windows AD account and name of the default domain (the default domain is the same domain that contains the majority of the Windows users, who are also BusinessObjects Enterprise end users). End users who do not have accounts in the default domain can still log on to BusinessObjects Enterprise, but they need to specify their domain names each time they log on.

Table 3
Administrator settings for Windows AD authentication in the CMC
The Mapped AD Member Groups section enables specification of which Windows security groups are permitted to access BusinessObjects Enterprise. Any Windows user who belongs to a mapped Windows security group can log into BusinessObjects. Users who are not members of at least one mapped Windows group can’t access BusinessObjects Enterprise unless the administrator specifically creates a BusinessObjects user ID for them within the CMC. To import a new Windows group to BusinessObjects Enterprise, an administrator types in the name of the Windows group (preceded by the group's domain or machine name) and clicks the Add button.
Windows AD authentication in BusinessObjects Enterprise supports two authentication methods, NT LAN Manager (NTLM) and Kerberos, one of which must be selected. Both authentication methods are supported within Windows AD, but Microsoft recommends the use of Kerberos authentication. Microsoft has developed Kerberos as the replacement to NTLM as the default authentication protocol in Windows AD, but NTLM is still widely used as a backup when a Windows AD domain controller is not reachable or available.
To configure BusinessObjects Enterprise for the Kerberos authentication method, a domain service account in Windows AD that is trusted for delegation must be available. This account is known to BusinessObjects Enterprise as the service principal name.
In Windows AD authentication, user passwords are not stored in BusinessObjects Enterprise, and it is the function of the Windows AD domain controller to verify passwords. Any time a user attempts to access and log on to BusinessObjects Enterprise, a password confirmation request is sent to the domain controller. BusinessObjects Enterprise then waits for successful confirmation of the request. If the user information authenticates properly in Windows AD, BusinessObjects Enterprise allows a connection and log-on.
SAP Authentication
SAP ERP is a bundle of business applications that focuses on ERP solutions. SAP ERP provides integration of information and processes, collaboration, industry-specific functionality, and scalability. SAP ERP is based on SAP’s technology platform, SAP NetWeaver, and contains various business-based modules. As SAP is typically used within a large portion of an organization, it can serve as a central location of users and passwords. Subsequently, SAP authentication allows the administrator of BusinessObjects Enterprise to leverage users and roles that exist in an SAP ERP system, and SAP authentication in turn allows for BusinessObjects Enterprise authentication with SAP ERP user information.
Administrators can configure SAP authentication in BusinessObjects Enterprise by selecting the SAP tab of the authentication page of the CMC. The SAP authentication configuration page then contains four tabs with specific details for the configuration of SAP authentication.
The Entitlement Systems tab of the configuration page contains the basic information for connecting to an SAP ERP system, including the name and client of the SAP system, the application server on which the SAP system resides, and the user name and password to connect to the SAP systems (Table 4). This user account is specific to the SAP authentication in BusinessObjects and needs to have a name that reflects its use by BusinessObjects to connect to an SAP system, such as BOBW_Connect.
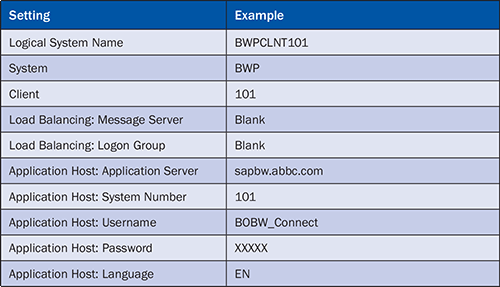
Table 4
Administrator settings for SAP authentication’s Entitlement Systems tab in the CMC
The Role Import tab of the SAP authentication configuration page contains the roles in the SAP system that can be made available for users of the BusinessObjects systems (Table 5). SAP roles are defined as collections of certain activities used in different business scenarios. In the normal course of business, each user is assigned with some activities and restricted from others to ensure that business data is always secure. Once the role is imported on this page, it shows as a group in BusinessObjects Enterprise. Imported roles then determine the data to which BusinessObjects users have access from the source SAP system.

Table 5
Administrator settings for SAP authentication’s Role Import tab in the CMC
The SNC Settings tab (Table 6) of the SAP authentication configuration page contains the settings to set up and enable Secure Network Communications (SNC) with the SAP system. SNC is a layer in the SAP software architecture that enables use of stronger authentication, encryption, and SSO. By default, SAP systems contain basic security measures that include user authentication based on passwords. With the use of SNC, security in an SAP system can be extended beyond basic measures to include additional protection offered by tougher methods. Configuration of SNC within the SAP authentication is optional.

Table 6
Administrator settings for SAP authentication’s SNC Settings tab in the CMC
The Options tab of the SAP authentication configuration page contains the specific settings and rules within BusinessObjects Enterprise for customizing the use of SAP authentication (Table 7). It includes the option to enable SAP authentication, maximum number of failed accesses, number of seconds to keep an entitlement system disabled, maximum number of concurrent connections, and number of uses per connection. It also includes options for whether users are automatically imported into BusinessObjects Enterprise and whether user information is synchronized between SAP and BusinessObjects Enterprise.

Table 7
Administrator settings for SAP authentication’s Options tab in the CMC
In SAP authentication, user passwords are not stored in BusinessObjects Enterprise, so it is the function of the SAP authentication service to verify passwords. Any time a user attempts to access and log on to BusinessObjects Enterprise, a password confirmation request is sent to the SAP authentication service, and BusinessObjects Enterprise waits for the successful confirmation of the request. If the user information authenticates properly in the SAP system, then BusinessObjects Enterprise allows a connection and log-on.
Adam Getz
Adam Getz currently serves as a Manager, Business Intelligence for CGI Federal. In this position, he is leading a large business intelligence and data warehousing implementation for a federal client. He is a thought leader in the field of information technology and an expert in the deployment of leading business intelligence, database management, and data integration products. He has presented at a variety of local, national, and international events, including the 2006 BusinessObjects International Conference, 2007 Oracle BIWA Summit, 2008 Oracle Open World, and 2010 and 2011 ASUG SAP BusinessObjects User Conferences. In addition, Adam is the creator and main author of bi-insider.com, a website, portfolio, and blog that provides rich technical and functional content to business intelligence and data warehousing professionals. He has also published numerous technology white papers that have focused on various topics within business intelligence and data warehousing. Adam currently serves as the chairperson of the Washington DC Business Objects User Group.
You may contact the author at adagetz@yahoo.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the editor.














