Webinar: SAP Cybersecurity Priorities
Webinar On-Demand
Meet the Experts
Key Takeaways
⇨ Keeping data stored in SAP systems protected is paramount
⇨ Investing in education and training is the primary strategy being used to address cybersecurity priorities
⇨ IT and security teams are the most likely to be setting cybersecurity priorities
View this webinar on- demand to dig deep in the SAPinsider research report:
Cyberattacks and cyber crime continue to grow across the globe. The latest statistics show growth in both the frequency and cost of attacks, and as many as two thirds of organizations may have experienced a cyberattack during the past year. With cybersecurity on the minds of many businesses, it is important to examine the cybersecurity priorities when it comes to their SAP systems. Earlier this year, SAPinsider research revealed that ransomware attacks, unpatched systems, and compromised credentials were the top three cybersecurity threats to SAP systems. This report will focus on what organizations are prioritizing to secure their SAP systems and how they are ensuring their teams are ready to meet these threats.
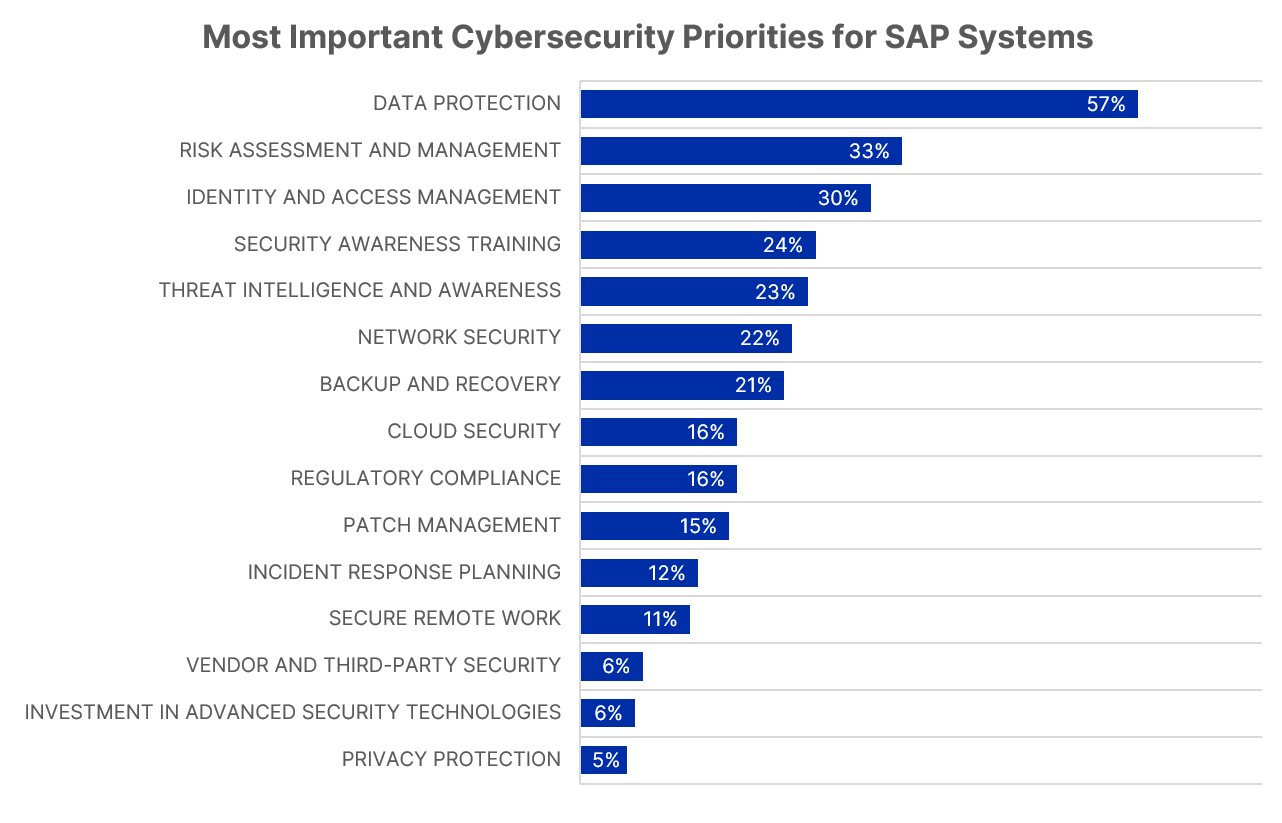
The survey asked the respondents to about their cybersecurity priorities, the teams involved in setting those priorities, how they are protecting their SAP systems, in which areas they are prioritizing cybersecurity investment, and the impact of the current economic climate on those priorities. Protecting the data in SAP systems remains the top priority for respondents (57%), with risk assessment and management (33%) and identify and access management (30%) much less important. This aligns with the fact that 53% of respondents reported that the biggest factor impacting their cybersecurity priorities is the need to keep sensitive and confidential data in SAP systems protected from potential threats.
 Robert Holland will discuss the full data analysis from 144 members of the SAPinsider community and you receive recommendations for your own plans.
Robert Holland will discuss the full data analysis from 144 members of the SAPinsider community and you receive recommendations for your own plans.
- Explore the factors that are most impacting cybersecurity priorities for SAP systems
- Learn about the actions being taken to support cybersecurity priorities
- Understand the types of security education and training being prioritized
- See the list of cybersecurity priorities and cybersecurity threats to SAP systems
Sponsored by:






