SecurityBridge
SecurityBridge is the leading provider of a comprehensive, SAP-native cybersecurity platform, trusted by organizations worldwide to safeguard their most critical business systems. Our platform directly integrates real-time threat monitoring, vulnerability management, and compliance capabilities into the SAP environment, empowering organizations to protect their data’s integrity, confidentiality, and availability with minimal manual effort. With a proven track record, including a stellar customer success rating and over 5,000 SAP systems secured globally, SecurityBridge stands out for its ability to accurately provide a 360° view of the SAP security posture, ease of use, rapid implementation, and transparent licensing.
Featured Solutions
-
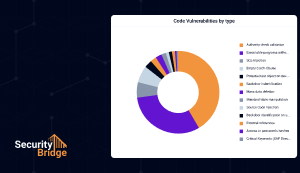
Threat Detection for SAP
Gain real-time visibility into SAP threats, centrally monitor malicious activities, and prioritize risks to protect critical systems. Guided Security provides up-to-date controls to help your team detect
-
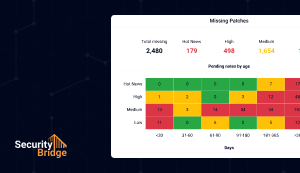
Patch Management for SAP
Reduce risk with timely SAP security patches and guided implementation of relevant Security Notes. Get tailored insights into their impact on your systems and streamline patching with automated or guided procedures, reducing workloads and enhancing security.
-
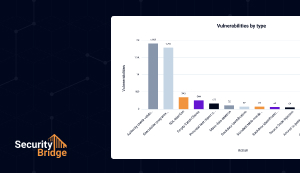
SAP Compliance Automation
Centralized compliance monitoring offers a unified view of system changes and their impact on SAP security and compliance. Preconfigured checks ensure best practices with minimal configuration, while integrated security events provide a 360° view of your security posture
Featured Content
-

Customer Stories
We are passionate about delivering a robust platform that makes our customers happy and, most importantly, secure. We act as an extension of the SAP team to drive security processes, and our customers love us for it
-
AI & SAP Security: Benefits, Risks and Prerequisites
Discover how integrating AI into SAP can enhance cybersecurity, while also understanding the associated benefits and potential risks.
-
Multimedia Center
-

Security Automation: The Need for a Last Line of Defense
Watch our webinar on Security Automation, featuring a special guest from Answerthink. Discover how you can automate your SAP security and compliance processes to improve your security posture and implement a last line of defense for your mission-critical SAP landscape.
-

Mastering NIST and CISA Compliance for SAP
Watch this enlightening webinar where we simplify the NIST and CISA regulatory frameworks, map CISA guidelines to SAP instances, and showcase how the SecurityBridge platform can assist you in achieving your SAP compliance needs.
Articles / Case Studies / Videos
-

SecurityBridge Appoints New CEO to Drive Global Expansion
Reading time: 2 mins
SecurityBridge has appointed Jesper Zerlang as CEO effective January 1, 2026, signaling a strategic shift toward global growth while the founders transition to roles focusing on product innovation and customer initiatives amidst rising demand for SAP-native cybersecurity solutions.
-

Securing SAP Systems: Strategies to Minimize Attack Surface and Protect Sensitive Data
Reading time: 3 mins
SAP systems, widely used and vulnerable, pose significant risks of cyber attacks due to configuration errors, access control issues, and software bugs, necessitating continuous monitoring and implementation of strong security measures to protect against exploitation. Fill the Form below to read the entire article.
-
-

Interventions for SAP Fiori Security
Reading time: 3 mins
This article highlights the importance of securing the SAP Fiori platform through measures such as encrypted communications, user authentication, local data storage protection, compliance with regulations, virus scanning, and protection against UI redressing attacks to ensure a safe and intuitive user experience.
-

The Ultimate Guide to SAP RFC: Streamlining Communication and Ensuring Robust Security
Reading time: 3 mins
The article highlights the importance of SAP Remote Function Call (RFC) for seamless integration and secure communication between SAP systems and external applications, emphasizing its benefits in automation, real-time data exchange, and security measures to protect against unauthorized access.
-

Enhancing SAP Security Through McCoy & Partners and SecurityBridge Collaboration
Reading time: 1 mins
To address the pressing need for SAP security, McCoy forged a strategic partnership with global SAP security provider SecurityBridge, a company sharing McCoy’s entrepreneurial spirit.
-

Why MSP PASàPAS Selected SecurityBridge To Protect Customers’ SAP Systems
Reading time: 1 mins
PASàPAS leverage and install SecurityBridge’s cybersecurity platform for SAP to help more SME organizations understand and mitigate the risk of hackers breaching their networks and stealing, damaging, or holding data hostage.
-

Sanofi Replaces Traditional SAP Security with SecurityBridge
Learn more from our customer Sanofi about how the SecurityBridge Platform helped them streamline and protect their SAP systems in this short video.
-
-

SAP BTP Security: A Top Priority for 2024
Reading time: 3 mins
he recent global SAP user conferences have revealed one common trending topic: SAP Business Technology Platform (BTP). SAP customers are about to adopt this platform for tailoring standard processes and creating integrations with their supply chains.
-

Remote Code Execution (RCE) Vulnerability in SAP
Reading time: 2 mins
Remote Code Execution (RCE) vulnerability in SAP is a type of security issue that allows an attacker to execute arbitrary code on a target system remotely. This means an attacker can exploit a vulnerability in a system’s software to access a remote system and execute commands or actions without authorization.
-

SAP BTP: Why your business platform needs security of the same kind
Reading time: 3 mins
SAP users understand that a technology platform connecting businesses to the world can also potentially increase the surface of cyber-attacks. Therefore, to protect such a platform, security of the same kind is needed, in other words, a security platform.
-
How will AI change the SAP cybersecurity threat landscape?
Reading time: 3 mins
Artificial intelligence has been a hot topic for many years and its applications span multiple industries. With the release of OpenAI’s GPT-3 language model, we have reached a significant milestone in the evolution of AI. This model can understand and generate human-like text with remarkable accuracy. As AI continues to advance, it has the potential…
-

How to Handle a Remote Code Execution (RCE) Vulnerability in SAP
Reading time: 1 min
[5:05 PM] Shawn Byers Excerpt: Learn how SAP Security Patch Day, understanding SAP attack vectors, and mitigating SAP risks are essential for safeguarding your systems. Stay proactive against Remote Code Execution vulnerabilities to protect your organization’s data and processes. Discover expert insights on reducing attack surfaces and applying timely patches to fortify your SAP environment.
-

The Cybersecurity Acronyms You Need To Know For Better SAP Security
Reading time: 2 mins
Sensitive data theft, disruption of mission-critical business processes, ransomware, and halt of all operations were warnings from the Cybersecurity and Infrastructure Security Agency (CIA) two years ago. The alert concerned severe security flaws, termed ICMAD (Internet Communication Manager Advanced Desync), affecting businesses using SAP.
-

Sanofi Replaces Traditional SAP Security with SecurityBridge
Reading time: 1 mins
Sanofi, a global biopharmaceutical company focused on human health, selected the SecurityBridge Platform to replace a traditional security tool that had been in use for three years. With a vast SAP enterprise, this was not an initiative that was taken lightly. In 2020 Sanofi took that decision based on concerns that their business requirements had…
-

The Patch and Vulnerability Management Symbiotic Relationship
Reading time: 1 mins
IT professionals turn to patch management and vulnerability management procedures to mitigate hackers. Each process is unique; however, both are frequently used. Vulnerability management covers many risks, whereas patch management concentrates on identifying relevant patches and timely implementing security-relevant software updates for specific bugs or faults. Vulnerability management and patch management are both required processes…
-

How to Use the S/4HANA Migration to Increase Your Security Posture
Reading time: 2 mins
“There are a few constants in life” – a statement that also applies to the SAP user community. It has always been a challenge for SAP customers to bring their large SAP environments to a current release level. Although the vendor has done a lot in the past to simplify this, it is still not…
-

How to use the SAP Expert Search to find SAP Notes
Reading time: 2 mins
After many years in the SAP eco-system, I know many good and bad practices exist in the IT Departments of – to be frank – every organization on this planet. Initiated by the SAP Security Patch Day in September 2022, our team has nudged me to share some knowledge. In this short how-to description, we…
-

5 Tips to Ensure your SAP Interfaces are Secure
Reading time: 4 mins
Security has become increasingly important as businesses rely more on technology and digital systems. One area of particular importance, which is an important topic at any SAP Sapphire, is the security of interfaces, which allows different systems and applications to communicate and exchange data. SAP interfaces play a role in integrating ERP systems, but they…
-

SecurityBridge – Case Study: SAP Security for the Pharmaceutical Industry
Reading time: 1 mins
Faced with resource restrictions and overwhelming amounts of data, this company needed a solution that could be implemented with little internal resources and within a tight schedule. This company had previously worked with a platform that produced false positive data that wasted time and resources to address.
-

SAPinsider Buyers Guide: Cybersecurity
Reading time: 1 mins
Cyberattacks and cybercrime continue to increase in frequency. In SAPinsider’s 2022 Benchmark Report on Cloud Security Trends for SAP Customers, nearly two thirds of respondents indicated their organization had experienced an incident targeting one of their cloud service providers. While these attacks may not always directly affect SAP systems, in an environment of increased digital…
