Introducing RFID to a shop floor, warehouse, or retail environment requires that the SAP professional learn about new kinds of hardware and standards. Discover the differences among the different RFID tags and readers, and see how you might integrate them into an SAP landscape.
Key Concept
The SAP Auto-ID Infrastructure (AII) integrates data from smart-item devices like RFID components with enterprise applications. SAP AII is part of the SAP NetWeaver technology stack and converts RFID data into business process information by associating it with custom mapping rules and metadata.
Deploying RFID involves selecting the right tags and readers as well as maintaining an IT infrastructure
that can process the data the hardware gathers. I will give you the basics of wireless supply chain technology and what it
entails in terms of hardware and software. I will also explain how you can use RFID and what it takes to implement the
technology. Then I will show you how it integrates with your SAP landscape.
RFID 101
In its most basic form, electronic tagging allows an object or location to be automatically identified at
a distance without a direct line of sight via an electromagnetic challenge/response exchange. In supply chain management
applications, the tagged object is usually a pallet, but it can be a box sitting on a pallet or even a single item inside
a box.
Readers and tags are at the center of any wireless system. The readers generate radio frequency (RF)
signals that serve a dual purpose: They transmit an interrogation message and supply power for those tags that need it.
The tag captures energy generated by the reader and executes the commands it has been sent.
The simplest command results in a reply containing a unique digital ID, which is processed by the system
connected to the reader. A variety of information, such as a name, manufacturer, SKU number, or pricing can be contained
in a tag, as can more complex data, depending on its construction.
Simple passive tags can store information about the tagged object, such as its serial number, electronic
product code (EPC), or details like manufactured date and product composition. More sophisticated active tags can perform
complex tasks like monitoring environmental conditions such as heat or humidity. The majority of RFID installations use
passive tags, which are considerably cheaper to purchase and maintain. Most of the information here pertains to passive
tags.
The EPC written on simple tags is
critical to any RFID system. Created to provide a path for businesses to migrate from bar-code technology to
RFID, this industry standard allows detailed product information to be moved quickly to anywhere in the supply chain. The
EPC infrastructure uses services such as Object Naming Service (ONS) to facilitate searching. EPC standards enable
automatic shipping notification and also have the potential to create new services. For example, a retailer could monitor
an ongoing promotional campaign using EPC and automatically lower prices as the campaign approaches its conclusion,
achieving the best results.
RFID Middleware
Large numbers of RFID tags in a warehouse or a retail store have the potential to generate massive data
loads that could bring an enterprise system to its knees. RFID middleware is the layer between the RFID readers and the
systems coping with the huge amounts product information. Like a traffic cop for RFID data, middleware allows unstructured
tag data taken from many RFID readers to be mapped precisely to the appropriate IT asset. SAP and many third-party vendors
offer RFID middleware to handle the data written to and read from RFID tags and integrate that data into business
applications.
Figure 1 paints a picture of middleware with a large brush. For the sake of simplicity, I have
shown the four major functions of middleware: data filtration, reader coordination, data routing and integration, and
process management. In reality, RFID middleware performs many different operations: basic data filtering, reader
integration and coordination, reader monitoring, false-read management, and integration with partner systems, providing
architecture scalability.
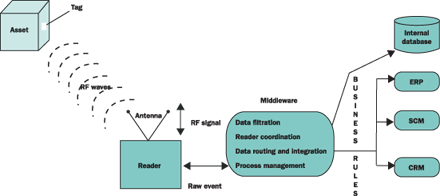
Figure 1
Typical RFID landscape including tag, reader, middleware, and ERP system
RFID in the IT Landscape
To incorporate RFID technology into your supply chain and improve efficiencies, RFID data from warehouses
and manufacturing facilities must be integrated tightly into your overall corporate IT infrastructure. You should evaluate
several key issues to make sure the
infrastructure can transform, enhance, and route the huge amount of data that needs to be accommodated.
Enterprise applications also need to access the RFID system to perform tasks such as managing inventory.
The RFID system must be able deliver data in the appropriate format immediately and with minimal
configuration
to your ERP, SCM, CRM, and other enterprise applications as well as to
databases and other systems. It must also manage metadata across these applications, maintain cross-
referencing relationships, and reliably manage and route information without interruption. In addition, the distributed
architecture must support the existing RFID data and have the capacity to meet the potential future demand as the number
of events triggered by more RFID tags grows. Future requirements may include tagging at the item level, more scanning
points in the supply chain, and more facilities creating and shipping products.
On top of the internal demands, the RFID infrastructure must support any
collaboration efforts your enterprise is involved in and be adaptable to handle the transfer and
synchronization of data and documents among business partners. RFID systems should support UCCnet-based data
synchronization and AS2-compliant EDI transactions. They should also be able to incorporate EPC data into advance shipping
notifications, purchase orders, and other documents. The infrastructure must be flexible enough to support interactions
ranging from a batch EDI push to dynamic query responses in real time.
To ensure the complete availability and crash-free operation of mission-critical applications distributed
across manufacturing and distribution facilities, the infrastructure must give administrators the ability to monitor and
manage the health of all of its components, including those that are directly or
indirectly associated with it.
RFID and SAP
SAP Auto-ID Infrastructure (SAP AII) integrates data from smart devices like RFID components with
enterprise applications. Part of the SAP NetWeaver technology stack, SAP AII converts RFID data into business process
information by associating it with custom mapping rules and metadata. These mapping rules can relay the incoming
observation data generated by the RFID system from the tags and readers directly to business processes running at the back
end on either SAP or non-SAP systems, which can then execute predefined business workflow, or simply record the data in a
database store for analysis later. In addition to integrating the back-end ERP and the supply chain management system, it
also supports object naming and Physical Markup Language (PML) as well as other services.
You can use various SAP CRM, SCM, SRM, and PLM applications with wireless systems to enhance supply chain
and asset management activities. In addition to SAP AII, noted earlier, SAP provides support to RFID systems with the
following:
- SAP Event Management (SAP EM) gives RFID data network visibility and monitors it across business
partners. It offers a complete history of all business processes related to tagged and non-tagged goods and is the key to
exchanging this information with your business partners.
- SAP Enterprise Portal offers a single, orchestrated view for RFID data and role-based access
both internally and externally for trading partners.
- ERP adaptors deliver "out-of-the-box" integration for existing SAP R/3 supply chain execution
processes and offers real-time visibility of the supply chain.
The ERP adaptors enable existing R/3 systems from Release 4.6 upward, including R/3 Enterprise 1.1 and
2.0, with the ability to accommodate RFID data. R/3 systems can process EPC data as well as delivery and handling
information with the adaptors. Business processes such as the packing, delivery, and unpacking of goods are supported.
These procedures result in automatic triggers that verify delivery and provide the capability of sending advance shipping
notifications to your business partners and more.
Goods Receipt Scenario
Let's look at how RFID fits into a typical SAP-based supply chain management implementation by following
a typical goods receipt process. It starts with receiving an inbound delivery from a business partner that
contains EPC package information. Figure 2 compares a typical goods receipt process without RFID versus using the
wireless technology.

Figure 2
Goods receipt process with and without RFID
With RFID, fixed readers installed on a receiving dock or handheld mobile readers collect the data.
Details of the inbound delivery can be seen in R/3 (and the document flow), which shows the inbound delivery has arrived,
and EPC information provides individual item details. SAP AII generates an IDoc using the expected date and time provided
by the purchase order, confirming that this is the expected event information. Details of delivery can also be sent to the
message monitor.
Next the R/3 system uses SAP Exchange Infrastructure (SAP XI) to send a sequence of messages to and from
SAP AII. This provides the capability to remap information in the IDoc to trigger different kinds of activities. SAP AII
can cope with many kinds of exceptional situations, such as shortages in a delivery or deliveries made erroneously. With
SAP EM integration, the assignment of that event is linked to actual item information, which can be sent back to the R/3
system via SAP XI. It then completes the goods receipt automatically and triggers any other actions or processes that are
required.
While I have focused on a simple process to make the solution more transparent and easy to follow, the
system can accommodate the demands of more complex scenarios. The RFID technology also can expand the boundaries of your
ERP system and make the supply chain more efficient with your vendors. SAP AII reduces the need to set up point-to-point
RFID data-sharing connections with trading partners and provides harmonized master data for RFID-enabled assets across
trading
networks.
Tags and Readers: The RFID Backbone
The evolution of RFID technology has resulted in a variety of tags and readers that can meet the demands of diverse environments and applications. A tag provides onboard internal data storage capabilities, which is generally electrically erasable programmable read-only memory (EEPROM), coupled with RF technology to send information such as an electronic ID to an RFID reader.
There are three basic types of tags:
- Passive tags require no onboard battery and can be read from a distance ranging from inches to yards. Because they have no power source, passive tags have an unlimited lifespan and typically carry no more than 2 KB of data.
- Active tags have an onboard battery to support larger read ranges and memory sizes that run up to 1 MB and can perform other chores such as monitoring environmental conditions. They also cost more per unit and are physically larger, with three- to five-year lifespans.
- Semi-passive tags use a battery to run onboard circuitry and are able to reflect more of the radio wave transmitted by the reader, overcoming some of the interference that plagues passive tags.
Tags are categorized by their capability to read and write data. The simplest are Class 0 tags, which are read only and used for electronic article surveillance (EAS) applications. Data is written once into the tag at the factory, and the memory is then disabled. Class 1 tags are write once, read many, and can be either factory- or user- programmed. Class 2 tags are the most versatile and allow data to be read and written into their memory. Class 3 tags are read/write and come with onboard sensors to record conditions such as temperature. They require onboard power and are either semi-passive or active. Class 4 tags are read/write active tags with integrated transmitters that communicate with other tags or wireless equipment without the presence of a reader.
RFID Readers
Readers — or "interrogators" as they are sometimes called — consist of a digital signal processor (DSP), network processor, power supply, and radio frequency module. Readers, which can be fixed or mobile, work like traditional radio transceivers. An interrogation signal is transmitted to the tags via the reader's antenna, which receives the tags' replies. The replies contain the data to be processed by your SCM technology. In addition to establishing a bidirectional data link with a tag and links to the network server, which filters the results of an interrogation, reader signals remotely power passive tags.
Support for competing tag protocols, including ISO, EPC, and proprietary standards, varies from reader to reader. Most manufacturers offer some degree of multi-protocol support, but no one reader supports them all. Network protocols such as TCP/IP and RS 485 also vary from reader to reader, as does the ability of the firmware to be upgraded via the Web or the network.
In addition to the reader's protocol support and ability to be upgraded, you should also look for features such as the ability to use various antennas to resolve polarity issues. Most readers use up to four antennas, which can be multiplexed, and it's a good idea to find a unit that can adapt antennas to meet environmental conditions using dynamic auto-tuning.
Reader frequencies vary from country to country, so you may not be able to use one model of reader at all warehouses in your supply network. The UHF frequency band is 902 to 930 MHz in the US, for example, and 869 MHz in Europe. Other hardware characteristics, such as power regulations, also vary by location.
Tag/Reader Communication
To receive energy and communicate with a reader, passive tags use one of two methods. Inductive, or "near-field," coupling uses a communication technique similar to that of magnetic fields stimulating current in a transformer. The magnetic field of the reader's antenna is employed to induce a signal in the tag. Inductive coupling is generally used by wireless systems that operate in the LF and HF frequency bands.
The second method is based on techniques similar to those used in radar applications and is known as propagation, or "far-field," coupling. The reader emits an electronic pulse that bounces off the tag, which contains an antenna that is highly reflective to electromagnetic waves. The data sent back to the reader passes through a directional coupler, which decouples and decodes the data from the pulse. As the name implies, far-field systems have longer read ranges and operate in the microwave band, which contains UHF frequencies. Frequencies play a big role in how well your wireless system works, and they are influenced by environmental factors. Lower frequencies, for example, are less prone to distortion when used around wet surfaces or metal, but have slower multiple-tag read rates. The physical size of the tag is affected by frequency, with the lowest frequencies requiring the largest passive tags.
Regardless of frequency, tag placement relative to the reader's electromagnetic field is a factor that can affect performance. The operating range can be cut in half if a tag is not polarized correctly with its reader. If the tag antenna is aligned vertically and the reader is sending out signals horizontally, only a small portion of the energy emitted by the reader will hit the tag antenna. The problem is similar to what you experience when trying to talk on a cellular phone in a closed room where the signal is weak. The reception can be improved dramatically by moving the phone and changing its orientation.
Polarization issues are unavoidable but can be overcome to a large extent by combining different techniques. A large number of tagged products will be oriented in various directions, and the reader will be unable to process some. Because the tagged products cannot be readily reoriented, the solution is to vary the position of the reader or build advanced antennas that are less sensitive to orientation. Many readers with diverse orientations relative to the read area can be used and sequenced to perform multiple scans from different directions. Tags are read individually at different times using the Time Division Multiple Access (TDMA) transmission technology to avoid cross-tag interference, and the results are merged, providing a much greater chance of identifying all of the tags present. Another solution employs a single reader with several switchable antennas that can be sequentially connected.
Shreekant W. Shiralkar
Shreekant W. Shiralkar is a senior management professional with experience on leading and managing business functions as well as technology consulting. He has authored best selling books and published many white papers on technology. He also holds patents for innovations. Presently he is global head of the SAP Analytics Centre of Excellence at Tata Consultancy.
You may contact the author at s-shiralkar@yahoo.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the editor.








