Jatin Grover explains how to provision access to an SAP system and SAP Enterprise Portal through a single access request when both of them have different user IDs for an employee in the organization.
Key Concept
The provisioning engine in SAP Access Control accomplishes user provisioning. Usually the provisioning happens either to a single user (one employee with a single user ID) in single or multiple systems or multiple users (different employees with a single user ID) to single or multiple systems.
This is a challenging scenario for which there are limited details available. Many of you may have struggled in the past if you faced this kind of scenario while doing implementations. I explain the complete scenario and the steps to be followed to realize it.
As mentioned above in my scenario the SAP system user ID and SAP Enterprise Portal user ID for the same employee are different. The SAP system places a restriction of 12 characters for a user name, whereas SAP Enterprise Portal could require more. Therefore, one alternative or workaround could be that the end user raises two different requests (i.e., one request for the SAP system and the corresponding role for provisioning and a second request for the SAP Enterprise Portal user and the corresponding role). This might not be feasible considering the extra effort required from the end-user perspective and redundancy.
There can be variations to this provisioning scenario. For example, in one scenario in GRC system customizing, the SAP system is set as a search and the detail data source with user data type is set with a value of SU01. (SAP Access Control uses the search data source system to search for users and the detail data source to retrieve user details.) In the request the end user adds an SAP ERP Central Component (ECC) role and SAP Enterprise Portal role for provisioning.
Another variation can occur in GRC system customizing. Active Directory is set as the search and detail data source. The SAP Enterprise Portal user management engine is Lightweight Directory Access Protocol (LDAP). In the request, the end user adds an ECC role and an SAP Enterprise Portal role for provisioning.
Configuration in both cases is similar, and the basic idea is also the same. An access request is created by specifying the SAP system user ID in the user ID field in the access request form. A standard field or any of the custom fields contains the SAP Enterprise Portal user ID that is used by GRC to provision the SAP Enterprise Portal role. The steps to take follow.
The SAP system is set as a search and detail data source with the user data type as SU01. In the request the end user adds an ECC role and an SAP Enterprise Portal role for provisioning.
Configurations
Steps 1 through 3 describe the prerequisites for this scenario.
Step 1. Maintain the Data Source Configuration
To maintain the data source configuration execute transaction code SPRO and follow menu path IMG > Governance, Risk and Compliance > Access Control > Maintain Data Sources Configuration.
In the subsequent screen under User Search Data Sources set the SAP system as the search data source. In the User Detail Data Source section set the same SAP system as the detail data source. In
Figure 1, GI7CLNT600 is set as the search data source as well as the detail data source. To do this, select the User Search Data Sources folder and click the New Entries button. Enter the connector id for your SAP system in the Target Connector field (e.g., GI7CLNT600). Populate the Sequence field and specify the User Data Type as SU01 by selecting the corresponding value using the help available for the field. After you enter this data, click the save icon to save the customizing.
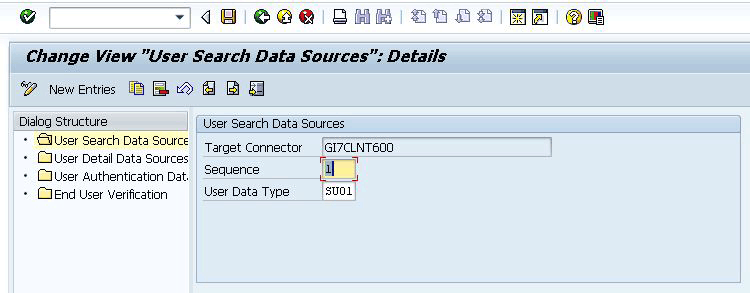
Figure 1
Maintain a user search and detail data source
Now select the User Detail Data Sources folder (refer back to
Figure 1) and click the New Entries button. Populate the fields in the right side of the screen just as you did before.
Step 2. Define Group Field Mapping of an Access Request Standard Field or Custom Field
To complete this step, execute transaction code SPRO and follow menu path IMG > Governance, Risk and Compliance > Access Control > Maintain Mapping for Actions and Connector Groups for portal connector. This action opens the screen shown in
Figure 2.
In
Figure 2, the User Alias field of the access request is mapped to the ID field. That means that in the access request the Alias field contains the SAP Enterprise Portal user ID to which the SAP Enterprise Portal role should be provisioned. To map the User Alias field of the access request to the ID, go to the Assign group field mapping section and click the New Entries button. Use the F4 key help available for the AC Field Name to select the USERALIAS value from the help result. Specify a value of id in the System Field Name and click the save icon to save the customizing.

Figure 2
Define group field mapping
You also define the group parameter mapping in the same configuration as shown in
Figure 3. Go to the Assign group parameter mapping section and click the New Entries button to add a Parameter Name and Parameter Value combination. After you have added all the combinations as shown in
Figure 3, click the save icon to save the customizing.
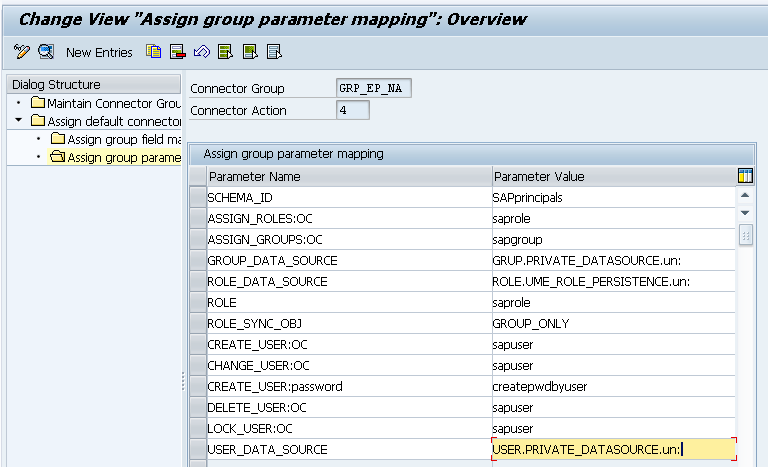
Figure 3
Define group parameter mapping
Step 3. Check User Details in the Detail Data Source System
As I described in step 2, the AC Field Name USERALIAS is mapped to the id field (
Figure 2). That means the field value of the User Alias field in the Detail data source system is the user ID in the SAP Enterprise Portal. To check the enterprise portal user ID value, execute transaction code SU01. In the screen that opens (not shown), enter the user ID in the User field and click the display icon

. This action opens the screen shown in
Figure 4.
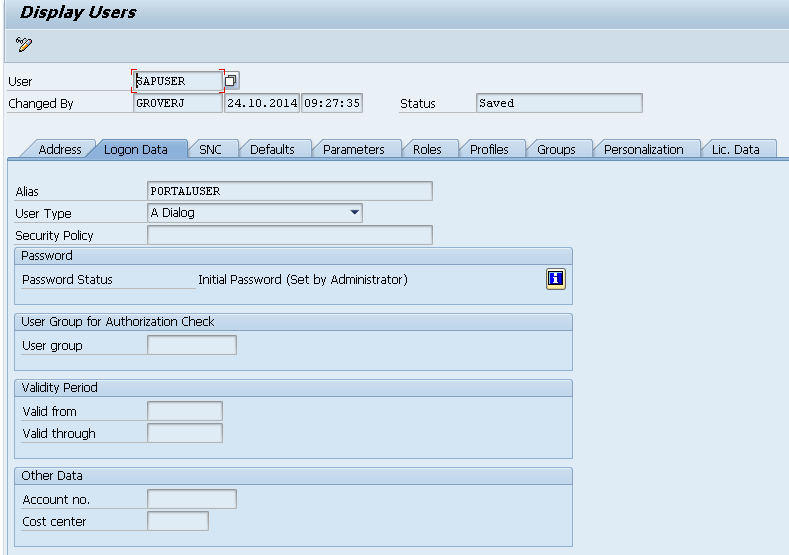
Figure 4
User Maintenance screen in the detail data source system
Click the Logon Data tab and check the value in the Alias field. If no value is in this field, then enter the corresponding SAP Enterprise Portal user ID; otherwise, the provisioning to the SAP Enterprise Portal will not be successful because the provisioning engine will not have any information regarding the user ID in the SAP Enterprise Portal. For example, in
Figure 4 for the user SAPUSER in the detail data source system, the Alias field contains the value PORTALUSER, which is the SAP Enterprise Portal user ID for the user SAPUSER in the SAP Enterprise Portal.
Request Creation
After an end user logs on to the GRC front-end user interface (UI) and launches the Access Request Creation link to create a request, the system retrieves user details automatically from the detail data source system (i.e., the SAP system settings that you configured in step 1 of the “Configurations” section) for the user for which the request is being created.
Figure 5 shows that all the user details, including the Alias field, are filled from the detail data source system for the user SAPUSER. As shown in
Figure 5, the value PORTALUSER is filled in the Alias field, which is the Alias field value (refer to
Figure 4) for the user SAPUSER. PORTALUSER is the user ID corresponding to SAPUSER in the SAP Enterprise Portal.

Figure 5
Access Request Creation form
The end user clicks the User Access tab and clicks the Add button to search the roles.
Figure 6 shows the searched roles. After adding the ECC role (e.g., AP_ACCOUNTANT) and the SAP Enterprise Portal role (e.g, CCROLE) into the access request, the end user clicks the OK button and clicks the Submit button to create the request.
Figure 7 shows the roles added into the request and request submission.

Figure 6
Search for roles

Figure 7
Submit a request with roles
Request Approval and Provisioning
The approver of the request opens the request for approval from his or her work inbox and approves the request by clicking the Submit button (
Figure 8).

Figure 8
Request approval
After the request is approved as explained above, open the GRC front-end UI via the SAP NetWeaver Business Client or the SAP Enterprise Portal and navigate to the Access Management work center. (The work center is visible to you after you open the GRC front end.) Click the Search Request link to open the Search Request screen (
Figure 9).
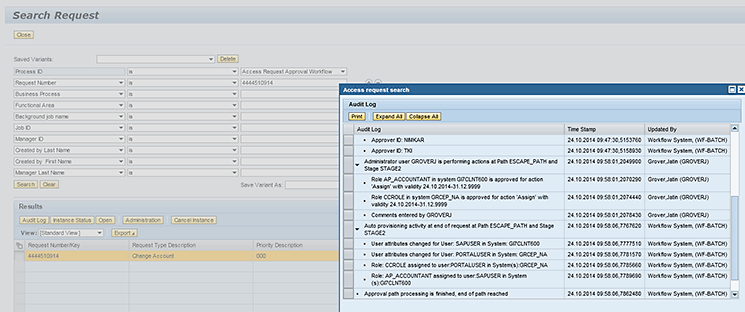
Figure 9
Search Request and Audit Log
In this screen, enter the request number mentioned in the success message during request submission (
Figure 8) into the field below the Request Number/Key column in the Search Request screen (
Figure 9). Click the Search button, select the row that appears as a result of the the search, and click the Audit Log button. A pop-up screen displays the Audit Log. The system now displays a message for provisioning of roles in the SAP system and SAP Enterprise Portal as shown in
Figure 9.
Log in to the ECC system and execute transaction code SU01. This action opens a screen (not shown) in which you enter the SAP user ID in the User field and click the display icon. In the Display Users screen (
Figure 10), click the Roles tab and check that the ECC role added during request submission has been provisioned.
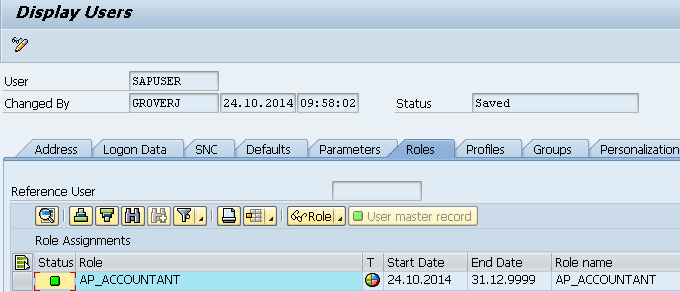
Figure 10
Role assignment after provisioning in the SAP system
Log in to SAP Enterprise Portal and navigate to User Management. Enter the SAP Enterprise Portal user ID in the Search field and click Go. Select the user and switch to the Assigned Roles tab as displayed in
Figure 11. Check that the SAP Enterprise Portal role added during request submission has been provisioned.

Figure 11
Role assignment after provisioning in the SAP Enterprise Portal
You can also check the assignments in GRC by logging on to the GRC front-end interface and clicking the Access Request Creation link. Enter the same SAP user ID for which the request was created before. Click the Existing Assignments button available in the access request form, and the system displays both the ECC role and SAP Enterprise Portal role as shown in
Figure 12.
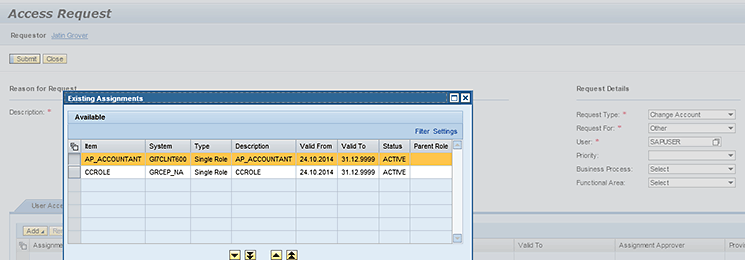
Figure 12
Existing assignments for the user
The roles from existing assignments can be added to the request for extension or removal as well. In addition to assignment of roles in the ECC system and SAP Enterprise Portal, the same methodology can also be used for other user actions such as User Creation, User Change, Locking, and Unlocking.
Jatin Grover
Jatin Grover is a senior developer for SAP Access Control, currently working with SAP Labs India Pvt. Ltd. He has vast experience with SAP products and worked on multiple SAP products (Supply Chain Management, Portfolio and Project Management, Project System, and Governance, Risk and Compliance) and technologies.
You may contact the author at
jatin.grov@gmail.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the
editor.



















