Learn how to configure and use the Configuration Validator tool for SAP Access Control 5.3 to diagnose issues with your company’s configuration or provide quick information to speed up the SAP support process.
Key Concept
The SAP Access Control Configuration Validator (ACCV) tool provides a summarized report of your current SAP Access Control configuration. It can be used to diagnose a current issue, provide periodic configuration checks, or provide a quick report to SAP support to speed up the support process. The report lists more than 53 different configuration checks and ranks the severity from low to very high. Additionally, you can configure certain aspects of the report to suit your company’s system or just provide a quick variant report of a targeted issue.
The SAP Access Control Configuration Validator (ACCV) tool helps you in diagnosing possible configuration errors with your SAP Access Control 5.3 system. It is designed to provide information to SAP support, but it can also be very useful for a company to use for a quick configuration check or a baseline of configuration before a system Support Package upgrade. Before using the tool, refer to “Technical Tips for the SAP Access Control Configuration Validation Tool” to determine if your company’s system is properly upgraded to the correct Support Package and whether it has the proper authorization to run it.
ACCV Tool: Configuration Validator
Once you are logged in to the ACCV tool, the first screen contains two tabs. The first tab is the Configuration Validator, with the sub-screen Configuration Validation Workflow. The second tab is named Administration. Customization of the screen via upload files is performed in the Administration tab.
Step 1. Select Checks
Within the Configuration Validation Workflow tab, the first screen consists of 53 SAP-delivered pre-defined checks that are already selected. They cover the SAP Access Control components compliant user provisioning (CUP), enterprise role management (ERM), risk analysis and remediation (RAR), and superuser privilege management (SPM). They are divided into the following categories (Figure 1):
- Back end: Installed Real-Time Agent (RTA) versions match, email, and other SPM back-end configuration checks
- Connector: CUP, ERM, RAR connectors, and SAP Access Control component name matching
- Data: Background jobs, number range issues, log level, RAR settings, and file paths
- Environment: SMTP settings, upgrade button, RTA version match, user access reviews (UAR) background jobs
- Web service: Checks Web services configuration settings for CUP, ERM, and RAR
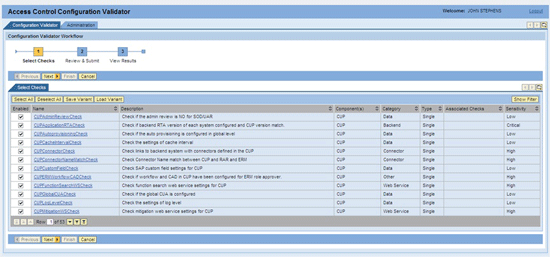
Figure 1
The initial screen within the Configuration Validation Workflow tab
The total number of checks per the SAP Access Control component is:
- CUP: 18
- ERM: 18
- RAR: 11
- SPM: 5
- Cross Component: 1
Those checks are defined and also assigned one of severity levels of Low, High, and Critical. They are also designated as a Single or a Composite (Cross Component) check. All the checks are pre-selected. Options are available to change the checks selected, unselect all checks with the Deselect All button, save a variant, or load a variant.
Additionally, a full description of each check is available by clicking the highlighted link itself. The details appear in a pop-up box (Figure 2).
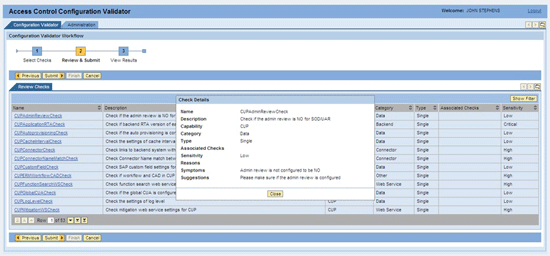
Figure 2
An example of the link description dialog box
Step 2. Review and Submit
After reviewing and selecting the checks to be validated, the user moves to part 2 of the workflow (the Review & Submit process). In this stage, the checks selected can be changed or the entire process can be cancelled. Click the Submit button and the tool automatically starts the validation process (Figure 3). This process can take several minutes to more than 30 minutes, depending on the number of checks that were selected.
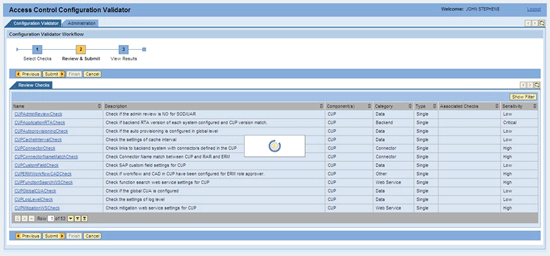
Figure 3
The ACCV tool screen: Review & Submit
Step 3. View Results
At the final stage, view the tool’s results on the screen or download them to a Microsoft Excel file to review, format, save, and send to SAP Support. Also, note the two additional columns for each check selected: Result and Reasons (Figure 4). You can correct failed checks if required and rerun the tool again to properly check the configuration changes. SAP Support can be engaged if failed checks are unable to be fixed.
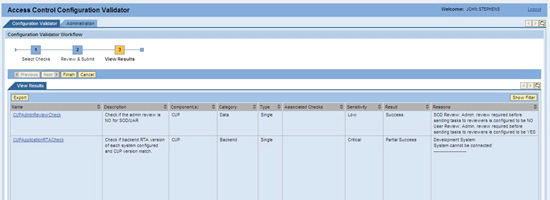
Figure 4
Tool results
Note
Clicking a check name provides you with a description of the check and suggestions on how it might be fixed. There are three result types:
1. Success: all configurations for that check passed
2. Failure: configuration for that check did not pass
3. Partial success: some of the configuration for that check passed
ACCV Tool: Administration
The tool provides a second tab for the administration of the configuration checks (Figure 5). For example, you can upload files to use to change the text for Configuration Check Names, Description, Severity Level, and the suggestions for fixing configuration failures. You can use this functionality to change or limit the availability of the checks performed by your system.
I recommend that you keep the following SAP Notes in mind when working with the SAP Access Control Open SQL Tool:
SAP Note 1168508: Compliant User Provisioning 5.3 Support Package (VIRAE) — For Support Package 12, the following issue is resolved:
- Error is received when trying to export the results from Configuration Validator Diagnostic Tool- Access Control 5.3. The following error is shown: /temp/webdynpro/web/sap.com/grc~accvwdcomp/Components/com.sap.grc.ac.cv.wdapp.CheckComp (Is a directory (errno: 21)).
For Support Package 16 Patch 4: The following issue is resolved:
For Support Package 17, the following issue is resolved:
SAP Note 1370400: Configuration Validator Diagnostic Tool — Access Control 5.3 — A guide for the ACCV tool
SAP Note 1534856: Unable to find the ViewACValidator action in the UME:
- Steps required for UME action assignment visibility
John Stephens
John M. Stephens is a senior SAP security and GRC consultant with Hermosa Beach Consulting Group. He has 15 years of SAP authorizations experience and has specialized in security implementations and upgrades of SAP GRC, SAP NetWeaver BW, SAP BusinessObjects, and SAP NetWeaver Portal over the last five years. Before joining Hermosa Beach Consulting Group, he managed teams to coordinate and performed SAP security implementations and administration activities within small, midsize, and large multinational SAP environments and operated as an independent consultant, performing SAP system audits, security implementations, and redesigns across many SAP applications.
You may contact the author at jstephens@hermosabeachconsulting.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the editor.








