Aman Dhillon explains how to secure your SAP systems from cyber attacks using SAP Configuration Validation.
Key Concept
Configuration Validation (CV) is a standard diagnostics tool available in SAP Solution Manager 7.0 and up. It enables companies to perform vulnerability checks to detect and remove security weaknesses in SAP systems. This includes vulnerabilities in areas such as security-relevant profile parameters, default Internet Communication Framework (ICF) services, password policies, Remote Function Call (RFC) destinations, and missing security notes in managed systems.
You’ve read the data sheets for third-party security tools targeted at SAP systems. You’ve listened to the sales spin. You’ve even seen the demo. But before you fire off the PO, ask yourself one question: Is there an alternative?
Starting in 2014, the answer is yes. The trigger for this change has been the rapid evolution of standard SAP components capable of detecting misconfigurations that lead to potential security risks. The most important of these components is Configuration Validation (CV), packaged in SAP Solution Manager 7.0 and above and delivered with standard license agreements (
Figure 1).
Figure 1
SAP CV
CV performs scheduled scans of managed systems in Solution Manager to automatically check for security vulnerabilities that may expose systems to cyber attacks. It integrates with End-to-End (E2E) Alerting to trigger email, short message service (SMS) alerts for high-risk issues, and management dashboards that provide near real-time information on the conformance of managed systems against security policies.
CV is a component of E2E Diagnostics and can be accessed through the Change Management and Root Cause Analysis (RCA) Work Centers in Solution Manager 7.1 (
Figure 2). The standard Solution Manager set-up process meets most of the prerequisites for using the component. This includes the installation and configuration of managed system adaptors and plugins such as ST-PI, ST-AP/I, and Diagnostics Agents. Configuration data from managed systems must be available in the Configuration and Change Database (CCDB) and extracted data should be available to InfoCube 0SMD_CA02 for analysis in Business Warehouse. SAP Note 1483508 (log-in required) provides full details of the prerequisites for RCA covering different versions and release levels of Solution Manager.
Figure 2
SAP Solution Manager Root Cause Analysis
The CCDB is the data source for CV. It is technically not an actual database but rather a collection of tables within the Solution Manager database that acts as repositories for configuration data from managed systems. This includes not just security-related data, but information on a wide range of areas that enables users to monitor and detect performance and other issues within SAP systems. Therefore, the value of CV reaches beyond security. However, for the purposes of this article, I am focusing exclusively on leveraging CV for vulnerability management.
Configuration data, including parameters, values, and change histories, is stored in containers within the CCDB known as config stores. These stores are updated through the Extractor Framework on an hourly or daily basis. Extractors only register changes to config stores in order to minimize storage requirements. The content of config stores can be browsed directly in Solution Manager or analyzed in drill-down SAP Business Warehouse reports through relevant InfoCubes.
Figure 3 provides a summary of the data flow.

Figure 3
SAP Configuration Validation data flow
Config stores are organized into groups for different subject areas, as well as aliases and sub-aliases. The ABAP-SECURITY group includes security-relevant stores for standard users, gateway server settings, Internet Communication Framework (ICF) services, Secure Network Communications (SNC) parameters, trusted RFC connections, table authorizations, and other areas.
The INSTANCE group includes the store ABAP_INSTANCE_PAHI, which contains the values of all active parameters in an ABAP instance. The RFC-DESTINATIONS group includes stores for reviewing attributes and configured users for RFC destinations. The group USER-AUTHORIZATION contains customizable stores for analyzing critical profiles, roles, and transactions. Security notes applied within managed systems are stored in the ABAP_NOTES store available in the ABAP-SOFTWARE group. Finally, the group J2EE SECURITY contains multiple stores for security-relevant properties in Java systems.
Certain changes in managed systems are event controlled and therefore include time stamps in managed systems. This includes implemented notes, changes to RFC destinations, and transport requests. Changes that are not event controlled are automatically assigned a time stamp when extracted into Solution Manager. Therefore, all configuration changes tracked in Solution Manager can be traced to specific dates and times.
Changes in managed systems for all config stores can be viewed using the Change Analysis tool. Changes are automatically flagged by this tool. Users can drill down for detailed information on each change including current and original values. The ability to perform detailed change analysis is one of the key advantages of security monitoring via Solution Manager as compared to third-party systems. Tools such as CV and Change Analysis enable customers to not only detect security vulnerabilities but pinpoint the root cause of changes that created the vulnerabilities.
Comparison of settings between two or more systems can be performed in the Report Execution tab of CV. Although comparison is supported between actual systems, SAP recommends using virtual systems to act as targets or references for comparison. This ensures that managed systems are compared to hardened and stable standards that reflect the security policies of each customer.
Best practice is to configure multiple reference or target systems with unique policies based on factors such as system type (ABAP or Java), environment (development, test, or production), and network zones (internal or external). Managed systems should then be grouped into comparison lists and validated against the relevant reference or target systems. CV is one of the few tools capable of performing such flexible, policy-based compliance reviews. Most third-party tools only support comparison against a standard vanilla benchmark.
Also, validation rules in third-party solutions tend to be hard-coded. This means users are not able to customize the parameters of the security checks performed by the tools to match their specific standards. Rules in CV, on the other hand, are transparent. Companies are therefore able to choose from a wide range of supported operators to validate security settings. This includes operators for value ranges, includes, does not include, equals, does not equal, between, less than, greater than, and other areas.
The most recent release of CV in Solution Manager 7.1 Support Package 11 enables users to weight security checks using a standard low-to-very-high risk scale. Reports can therefore be filtered to focus on high and medium risk items.
CV can perform consistency checks for managed systems using all the config stores available in reference systems. It can also enable users to focus on specific stores and items by filtering for variables before report execution. Reports are displayed in an integrated instance of SAP Business Warehouse and can be exported into Excel, HTML, and other formats for offline analysis. Non-compliant areas are color-coded for quick identification. Results support drill-down analysis for areas that violate security standards and can be filtered to remove compliant items. See
Figures 4,
5, and
6 for a report summary, a report, and report detail, respectively.

Figure 4
SAP CV report summary
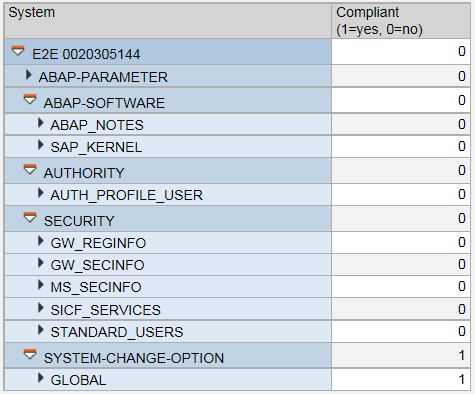
Figure 5
SAP CV report

Figure 6
SAP CV report detail
Since config stores are updated by default once a day, reports should be scheduled to execute on a daily basis immediately after the stores have been refreshed. This is performed in the Report Directory option of the Report Execution tab.
Figure 7 displays the on-screen options in the Report Directory.

Figure 7
SAP CV report scheduling
SAP-delivered templates in E2E Alerting should be used to automatically generate alerts for critical changes and non-compliant areas detected through CV. This includes areas such as changes to RFC destinations and ICF services, expiring certificates, and users with critical profiles. Conditions for alerts can be customized by adjusting metrics for managed objects. Alerts can be viewed in System Monitoring and the Alert Inbox, and notifications can be transmitted via email and SMS (
Figure 8).

Figure 8
E2E Alerting: Alert inbox
SAP delivers three security apps through the standard Web Dynpro dashboard application in Solution Manager (
Figure 9). They are located in the Cross-Application section for dashboard apps. The first is the Security Overview app, which summarizes security policy compliance by system across landscapes. The second, known as the Security Details app, displays compliance levels for software, configuration, and user categories. The third is the Security List app. This is used to convey security compliance levels for every SAP system ID. Dashboards apps can be automatically refreshed as often as every five minutes to provide security information in near-real time.

Figure 9
Security dashboard
Aman Dhillon
Aman Dhillon is an SAP security architect at Layer Seven Security (
www.layersevensecurity.com). Layer Seven Security serves customers worldwide to secure SAP systems from cyber threats and unlock the potential of Solution Manager for security monitoring. The company is headquartered in Toronto and is an SAP Services Partner.
You may contact the author at
adhillon@layersevensecurity.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the
editor.














