SAPinsider Buyers Guide Webinar: Cybersecurity
Webinar On-Demand
Meet the Speakers
Key Takeaways
Organizations are increasingly focused on fortifying their SAP environments against a variety of threats and often demand customized solutions, strategies, and approaches to protect against threats.
Tailored exclusively for the SAPinsider member community, the Cybersecurity Buyers Guide serves as a critical resource and offers valuable insights, expert recommendations, and Vendor Capability Assessments to equip community members with the essential knowledge and tools needed for intelligent and informed decision-making regarding cybersecurity practices and strategies.
The guide presents a detailed overview of the capabilities, services, and solutions offered by Technology Vendors, Infrastructure Providers, and Consultants and Integrators, enabling SAPinsiders to gain a clear understanding of the diverse options available and assess vendors that are best suited to meet their specific requirements.
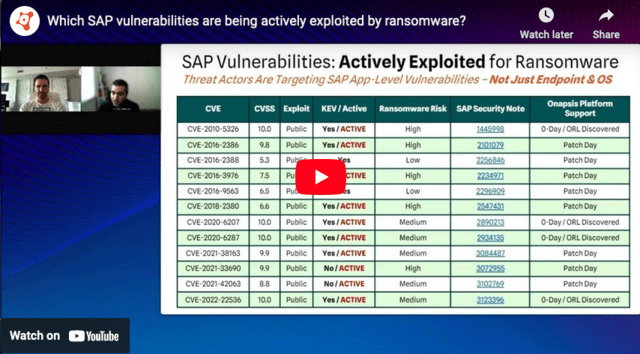
Cyberattacks and cybercrime continue to increase in frequency. In SAPinsider’s 2022 Benchmark Report on Cloud Security Trends for SAP Customers, nearly two thirds of respondents indicated their organization had experienced an incident targeting one of their cloud service providers. While these attacks may not always directly affect SAP systems, in an environment of increased digital risk, securing data in SAP systems stands out as a critical focus for many businesses. Highlighting this concern, SAPinsider’s 2023 Cybersecurity Threats to SAP Systems report identified ransomware attacks, vulnerabilities due to unpatched systems, and compromised credentials as the primary threats to SAP systems. In the broader context of cybersecurity, data protection within SAP systems is of utmost concern.
This emphasis is reasonable considering the critical data housed in these systems that form the core assets of a company, covering essential elements like partner and customer information, financial documents, transaction records, banking connections, and even personal identifiable information of employees. Considering the immense value of this data, it is logical why data protection is prioritized over other cybersecurity areas. For example, SAPinsider’s SAP Cybersecurity Priorities research report reveals that 58% of respondents from larger organizations and 54% from smaller ones ranked data protection as their foremost cybersecurity concern, highlighting its universal importance across various business scales. Aligning with these priorities, 53% of respondents identified the protection of sensitive and confidential SAP data as the primary driver of their cybersecurity strategies.
Explore related questions
To help SAP users in their cybersecurity decisions, SAPinsider put together this Buyers Guide, which aims to explore the challenges, opportunities, and trends in the cybersecurity space and to highlight key vendors and partners operating in the domain. The vendor capability assessments are intended to aid and assist organizations in selecting the vendors offering technology and consulting services for cybersecurity including capabilities around threat intelligence and detection, access and identity management, data protection and encryption, vulnerability management, incident response and forensics, cloud security and compliance, and secure code and application review.
Featured Vendors
![]()
![]()