The Power of Prevention
By Aditi Kulkarni, Product Security Senior Specialist, SAP Labs India
Unpatched vulnerabilities in systems are one of the primary factors that cause cyberattacks today. We don’t need to look far back to recollect the nightmare caused by the WannaCry ransomware attack in 2017. While the software vendor had released patches previously to close the vulnerability, much of WannaCry’s spread was from organizations that had not applied imperative patches or were using older end-of-life systems.
Then, in 2020, the unprecedented advent of COVID19 forced organizations to restructure their workforce management and impacted the way normal patching operations were conducted. Organizations had no time to plan for such a scenario, leaving their systems open to potential vulnerabilities that threat actors could easily misuse.
In our new normal of remote and cloud environments and rising cyber risk from more sophisticated threat actors, it is more critical than ever for organizations to prioritize their patching strategy.
How SAP Addresses Security – And How Customers Can Help
By ensuring that products are developed, tested, and delivered in the most secure way, SAP’s teams continuously work on enabling security by default in SAP products. But there is no such thing as flawless software.
At SAP, the Product Security Response Team (PSRT) collaborates with external security researchers for responsible disclosure of vulnerabilities identified on SAP products. These researchers can send their findings to SAP through a form or by directly writing to secure@sap.com. Besides showing appreciation to the external researchers for helping secure SAP products, the PSRT also coordinates private Bug Bounty programs on BugCrowd, HackerOne platforms.
While vendors do much to limit risk through vulnerabilities, customers too need to play an active role in safeguarding their assets and data. SAP periodically publishes new security patches to vulnerabilities on SAP products. It is important that these patches are applied by SAP’s customers. In the next few sections of this article, you will read about Security Notes, Security Patch Day, SAP services that help SAP customers stay updated about security patches, and recommendations for how SAP’s customers can plan their patching strategy.
Continuous Monitoring and Updates through SAP Security Notes
New security patches that need to be applied by SAP’s customers are published as Security Notes (Note: This portal is accessible only to users having S-User ID.) on the SAP Support Portal (see Figure 1). A Security Note can contain patches to one or more vulnerabilities for a certain SAP product. They include details about the vulnerabilities, their impacts, relevant patch description, and product versions.
Exploitability risk and impact of a vulnerability on a product is currently evaluated at SAP using Common Vulnerability Scoring System (CVSS) Version 3. CVSS is an open industry standard, initially developed by the National Infrastructure Advisory Council and continuously improved by the Forum of Incident Response and Security Teams, which consist of teams and companies all over the world. Based on the evaluated CVSS score, a vulnerability is categorized as Hot News, which corresponds to ‘Critical’ in CVSS severity rating scale, or as High, Medium, or Low. Consequently, a Security Note’s severity is decided by the severity of the most critical vulnerability that it patches.
SAP Security Notes are categorized in two ways
1. Patch Day Security Notes contain patches to vulnerabilities of Hot News severity and to vulnerabilities of High, Medium, or Low severities reported by customers or external researchers. 2. Support Package Security Notes contain patches to vulnerabilities of High, Medium, and Low severities found internally by SAP. SAP primarily consolidates all security patches to vulnerabilities found through internal quality assessments in Support Packages. However, a small subset of these are prerequisite to other functional notes that are released as individual corrections. Therefore, as an exception, security notes that are prerequisites to functional notes are released as Support Package Security Notes.
A Security Note might undergo an update after its release, for example, to enhance the description about the solution. SAP decides how and when to update a Security Note after analyzing its need, and each update undergoes quality reviews. An updated Security Note contains information about what was changed.
If a product is under maintenance, SAP releases security patches covering product maintenance versions released within the last 24 months. This is for vulnerabilities of Hot News or High severity. For vulnerabilities of Medium or Low severity, patches are released at least for the latest version of the product.
Read more about maintenance strategy here.
Some SAP products offer Customer Specific Maintenance (CSM) for product versions that are out of maintenance. If a vulnerability is patched on a product that has a version that went out of maintenance, then the Security Note will cover the out of maintenance version for the next one year. This is applicable for vulnerabilities of Hot News, High, and Medium severities.
Read more about SAP Security Notes here.
Setting an Example: SAP Security Patch Day
To help customers plan a consistent patching strategy, SAP releases its Security Notes on the second Tuesday of every month, the company’s Security Patch Day. Patch Day Security Notes are typically released on Security Patch Day, along with Support Package Security Notes and Update Notes. Scroll down on the SAP Security Notes page to view planned Patch Days for 2021.
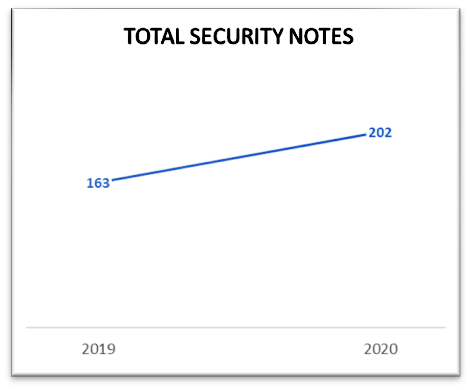
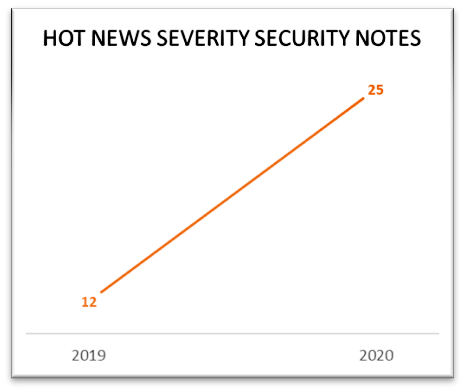
In 2020, SAP completed ten years of conducting Security Patch Days. A steady increase in the number of Security Notes released over the years corresponds proportionally to the increased awareness about software security in the industry.
Compared to the year 2019, 2020 saw an increase by 24% in the total number of Security Notes released, and an increase by more than 100% in the number of Hot News Security Notes released (see Figure 2).
These numbers make it evident that SAP software consumers must keep their SAP landscapes secure from external threat actors by applying patches regularly. In the next few sections, we will see how these released SAP Security Notes can be consumed by SAP customers.
Accessing SAP Security Notes
The complete list of SAP Security Notes and the information in each Security Note can be accessed in the SAP ONE Support Launchpad. (Note: This portal is accessible only to users having S-User ID.) S-User ID is a unique identifier that allows an SAP user to log in to report an incident, download software, configure connections, and more. An S-User ID contains the letter ‘S’ followed by a string of numbers.
An extended search option is also available in SAP ONE Support Launchpad via Expert Search, which provides multiple filtering options to identify Security Notes of each user’s interest. SAP Security Notes can be accessed via Expert Search and by filtering the Document Type as SAP Security Notes.
Public Disclosure of SAP Security Notes
Transparency is a key pillar of SAP’s security strategy. While access to SAP Security Notes is limited to S-User IDs, SAP also publicizes the patched vulnerabilities through the following channels:
Common Vulnerabilities and Exposures (CVE) Publications — These publications are considered an industry standard and a mechanism to publicly disclose patches to vulnerabilities. SAP became a CVE Numbering Authority in 2017, and since then publishes CVEs for all vulnerabilities patched via Patch Day Security Notes. The release of CVE disclosures is aligned with SAP’s Security Patch Day.
SAP Security Patch Day Blogs — These blogs are publicly accessible on The Official SAP Product Response Space, and contain details about released Patch Day Security Notes, their respective CVE, SAP product versions for which the Security Note is released, and their severity and CVSS ratings.
Security Spotlight News — SAP’s PSRT carefully monitors if a certain vulnerability, patched by SAP Security Note, has been gaining special attention of external threat actors and poses risk of unpatched systems getting exploited. If such an instance is identified, Security Spotlight News is published to call for immediate action to apply the SAP Security Note. The Security Spotlight News is publicly accessible.
Managing SAP Security Notes with SAP Tools
Several tools and services are available to help technical experts on the customer side identify the notes relevant for their landscape, analyze whether applying an SAP Security Note has side-effects on the system, and confirm whether application of the SAP Security Note was successful. These tools can be used individually, as well as integrated with other SAP tools for optimum usage. These tools include:
System Recommendations — enables organizations to automatically identify SAP Security Notes that are relevant to them. Read more about the tool here.
SAP Usage and Procedure Logging (UPL) — aids in the gathering of system usage data to easily identify SAP Security Notes addressing unused components. Read more about the tool here.
Business Process Change Analyzer (BPCA) — helps in efficient testing after applying an SAP Security Note by determining the business processes affected by the SAP Security Note. Read more about the tool here.
Configuration Validation — assists in validation after applying SAP Security Note; for example, by validating if a selected SAP Security Note has reached the production systems. Read more about the tool here.
SAP EarlyWatch Alert — helps in identifying resource bottlenecks, misconfigurations, and security problems. By verifying the security checks in the Alert’s report, organizations can proactively prevent severe security problems. Read more about the Alert here.
SAP Security Optimization Services
SAP Security Optimization Services (SOS) ensures smooth operation of a customer’s SAP solution by acting proactively, before severe security problems occur. As part of these services, an expert team of security consultants publishes the SAP Security Notes Advisory on Support Portal after every Security Patch Day. The Advisory contains detailed analysis of each SAP Security Note, risk of not implementing it, recommended implementation process according to the experts, and expected downtime during implementation.
In addition to the Security Notes Advisory, a monthly Security Notes Webinar is conducted by the experts. In this webinar, the experts explain every security note to the attendees, including the implementation method. Learn how to register for this webinar by visiting this page.
Both Security Notes Advisory and Security Notes Webinar services are available, without extra cost, to all customers of SAP, who are encouraged to take advantage of the information provided through these services.
Support Launchpad Notification
Security Notes classified as Hot News contain patches for critical vulnerabilities. SAP Support Launchpad provides an option to manage notifications for Security Notes with severity Hot News. Based on the mode of communication that the user opts for, a notification is sent in Launchpad or on-the-go via e-mail or SMS.
Design a Patching Strategy to Fit Your Needs
Every organization should have a systematic plan to apply security patches released for the products they are using, with a primary patching strategy goal of finding a balance between addressing security risk and business risk. Organizations can reduce the risk of exploitation from threat actors by applying the SAP Security Notes as they are released, staying current with patches, trends, and advice.
However, in practicality, it might be challenging for an organization to apply all SAP Security Notes released every month at once. The following practices may help customer organizations overcome this challenge.
Analyze — Schedule a periodic analysis of the released Security Notes. Leverage SAP tools and services to identify the relevant Security Notes, estimate the effort involved to apply those Security Notes, and understand the risk posed by not applying them.
Clarify — Additional information may be required to understand the relevance of Security Notes. Every Security Note with Hot News severity includes a document containing frequently asked questions, which can provide more clarity. Additionally, SAP’s customer support channel can be utilized to report customer incidents and get real-time support from experts.
Prioritize — Because Patch Day Security Notes are for vulnerabilities reported by sources external to SAP, there is a higher risk that these vulnerabilities are exploited by an external threat actor on unpatched systems. Security Notes should be prioritized by organizations considering this risk, along with the severity of the vulnerabilities. Security Notes with Hot News severity should always be considered with greater priority.
Decide — Primarily, there can be two ways to secure SAP systems: apply SAP Security Notes, or upgrade to the latest, secure product version. Security Notes identified as higher priority should be applied without delay. This step can be scheduled every month.
The Security Notes that are identified to be of lower priority need not be applied immediately. Instead, the product can be upgraded to the latest version in the next maintenance cycle. This decision, however, should be carefully made, as any disclosed vulnerability has a risk of being exploited in unpatched systems.
Apply Workarounds — SAP provides workarounds as part of the solution in some Security Notes if it is technically feasible. The feasibility is determined by the customer’s efforts involved in applying the workaround. If Security Note cannot be immediately applied due to the efforts involved, SAP recommends applying the workaround, which can temporarily prevent the occurrence of the vulnerability in the product. However, a workaround is only temporary until the actual patch in Security Note is applied.
Schedule Maintenance — All security corrections, including those found by SAP’s internal QA processes, are consolidated in Support Packages (SP) and in the latest version of an SAP product. Organizations are advised to update to the latest SPs or product versions by scheduling a maintenance cycle to ensure that their systems are secured.
Collaborations by SAP’s Product Security Response Team
As helpful as the above tools are, people power SAP’s security as well. SAP’s PSRT collaborates with developers, quality reviewers, customer support, and other internal SAP teams to ensure that quality Security Notes are released to SAP’s customers. Based on the severity of the vulnerability, strict timelines are assigned to patch the vulnerability. All of the involved entities in SAP work collectively to provide patches regularly and to publish Security Notes for SAP’s community.
Along with SAP’s internal teams, SAP’s PSRT also collaborates with various external researchers and research companies to ensure responsible disclosure of vulnerabilities. The team also coordinates private Bug Bounty programs on BugCrowd and HackerOne platforms.
When customers report vulnerabilities to SAP by creating customer support incidents, PSRT engages in the process of driving these vulnerabilities to closure and also coordinates customer-initiated penetration test reports on SAP’s cloud solutions.
In addition, SAP PSRT collaborates with governmental agencies like US CISA and German BSI to ensure accurate and synchronized alerts to SAP’s customers about critical SAP Security Notes.
Conclusion
Although SAP continues to keep security of its customers as a priority, it is equally important that the released security patches are applied in a timely manner to secure SAP systems. You can help prevent your SAP systems from getting hacked by instituting a monthly or at least quarterly Security Patch Day at your organization by following the updates and advice in SAP Security Notes and the patch disclosures. By having a systematic plan for patching at your organization, you can take an active role in reducing risk. Be sure to prioritize vulnerabilities identified as high-risk in the Security Notes, updating right away, while deciding which lower-risk vulnerabilities can be patched or can wait until your next upgrade. Finally, you should plan to update to the latest SPs or product versions by scheduling a maintenance cycle to ensure that your systems are secure.






